Office365 Executive Inboxes Targeted In Multi-Million Dollar Hacking Scheme
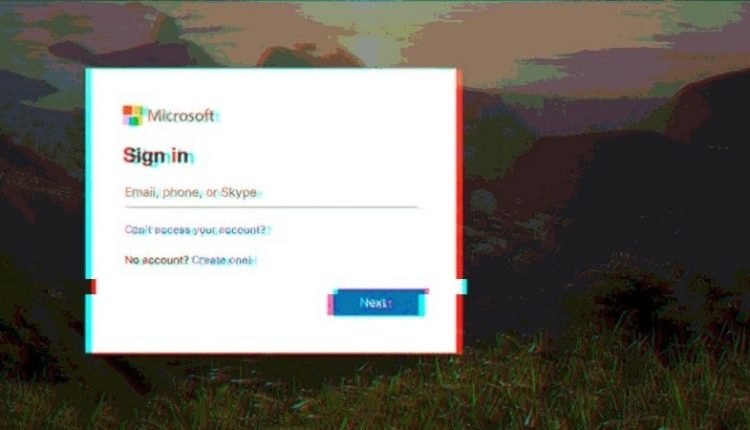
Table of Contents
The Modus Operandi: How Hackers Targeted Office365 Executives
The hackers behind this multi-million dollar scheme employed a multi-pronged approach, leveraging a combination of sophisticated techniques to gain access to highly sensitive executive accounts.
Phishing and Spear Phishing Attacks
The primary attack vector was a series of highly targeted phishing and spear phishing emails. These weren't your typical spam emails; they were meticulously crafted to appear legitimate and bypass initial suspicion.
- Subject lines: Emails used subject lines mimicking urgent business matters, such as "Contract Amendment," "Important Financial Documents," or even personalized greetings using information gleaned from social media or company websites.
- Attachment types: Malicious attachments included seemingly innocuous documents (.docx, .pdf) containing macros that downloaded malware upon opening, or links to compromised websites designed to steal credentials.
- Social Engineering Tactics: Hackers used sophisticated social engineering techniques to pressure recipients into immediate action. They employed urgency ("This requires your immediate attention!") and authority ("This is from the CEO's office"), exploiting psychological vulnerabilities to bypass security protocols.
- Compromised Accounts: In some cases, hackers leveraged previously compromised email accounts to lend credibility to their phishing attempts. An email seemingly originating from a trusted colleague or business partner significantly increased the likelihood of a successful attack.
Exploiting Vulbilities in Office365
While Microsoft continuously updates Office365 security, the hackers may have exploited known (or unknown at the time) vulnerabilities within the platform. Although specific vulnerabilities haven't been publicly disclosed in this particular case, potential avenues of attack could include:
- Outdated plugins or add-ins: Outdated software can contain security loopholes hackers can exploit.
- Weakly configured security settings: Insufficiently configured security policies within Office365 could have been exploited to gain unauthorized access.
- Unpatched software: Failure to regularly update Office365 applications and operating systems left systems vulnerable to known exploits.
Credential Stuffing and Brute-Force Attacks
In addition to phishing attacks, credential stuffing and brute-force attacks may have played a role. These methods involve:
- Credential Stuffing: Using lists of stolen usernames and passwords obtained from previous data breaches to attempt logins to Office365 accounts. If an executive reused passwords across multiple platforms, this approach could prove successful.
- Brute-Force Attacks: Systematically trying various password combinations until the correct one is found. While strong passwords make this approach time-consuming, it remains a viable threat.
The Financial Ramifications: The Multi-Million Dollar Impact
The consequences of this hacking scheme were devastating, resulting in significant financial losses and reputational damage.
Types of Financial Losses
The financial impact extended beyond a single loss event.
- Wire Transfer Fraud: Hackers were able to intercept and redirect funds through fraudulent wire transfers.
- Ransomware Attacks: Following the initial breach, some victims experienced ransomware attacks, resulting in further financial losses and operational disruption.
- Intellectual Property Theft: The compromise of executive inboxes may have led to the theft of sensitive intellectual property, confidential business plans, and other valuable company assets.
- Lost Contracts: Compromised communications could have led to the loss of important business contracts, leading to substantial financial penalties.
Reputational Damage
The repercussions went beyond financial losses; the incident caused severe reputational damage.
- Loss of Customer Trust: News of a data breach can significantly erode customer trust and damage brand loyalty.
- Negative Media Coverage: Negative media attention surrounding the incident further amplified the reputational damage.
- Impact on Investor Confidence: The incident could negatively impact investor confidence, potentially leading to a decline in the company's stock value.
Protecting Your Office365 Executive Inboxes: Prevention and Mitigation Strategies
Protecting your organization from similar attacks requires a multi-layered security approach.
Strengthening Password Security
Robust password security is paramount.
- Strong, Unique Passwords: Enforce the use of strong, unique passwords for all Office365 accounts. Passwords should be long, complex, and not reused across different platforms.
- Password Managers: Encourage the use of password managers to help employees securely generate and manage complex passwords.
Implementing Multi-Factor Authentication (MFA)
MFA is critical for enhanced security.
- MFA Methods: Implement MFA using methods like one-time codes, biometric authentication, or security keys. This adds an extra layer of security, even if passwords are compromised.
Security Awareness Training for Employees
Education is key to preventing phishing attacks.
- Training Programs: Implement comprehensive security awareness training programs to educate employees about phishing and social engineering tactics. Regular training and phishing simulations can significantly improve employee awareness.
Regular Security Audits and Monitoring
Proactive monitoring is crucial.
- Security Audits: Conduct regular security audits to identify and address vulnerabilities within your Office365 environment.
- SIEM Systems: Utilize Security Information and Event Management (SIEM) systems to monitor network activity and detect suspicious behavior.
Utilizing Advanced Threat Protection (ATP)
Leverage Microsoft's advanced security tools.
- Microsoft ATP: Microsoft's Advanced Threat Protection (ATP) offers advanced threat detection and prevention capabilities, including anti-phishing and anti-malware protection.
Conclusion: Securing Your Office365 Executive Inboxes from Future Attacks
This multi-million dollar hacking scheme underscores the critical need for robust security measures to protect Office365 executive inboxes. The methods employed—sophisticated phishing, potential vulnerability exploitation, and credential stuffing—highlight the importance of a layered approach to security. The financial and reputational damage suffered by victims emphasizes the necessity of proactive measures, including strong password policies, mandatory multi-factor authentication, comprehensive security awareness training, regular security audits, and the utilization of advanced threat protection services like Microsoft ATP. Don't wait for a devastating breach to occur. Take immediate steps to secure your Office365 executive inboxes and prevent Office 365 executive email breaches. Invest in robust Office 365 executive inbox security today and protect your organization from the devastating financial and reputational consequences of a cyberattack.

Featured Posts
-
 Mia Farrows Urgent Message Following Trumps Congressional Address Democracys Future At Stake
May 24, 2025
Mia Farrows Urgent Message Following Trumps Congressional Address Democracys Future At Stake
May 24, 2025 -
 The Untold Story Sam Altman Jony Ive And A Top Secret Gadget
May 24, 2025
The Untold Story Sam Altman Jony Ive And A Top Secret Gadget
May 24, 2025 -
 Stitchpossible Weekend A Potential Record Breaking Box Office Clash In 2025
May 24, 2025
Stitchpossible Weekend A Potential Record Breaking Box Office Clash In 2025
May 24, 2025 -
 Apples Stock Price Should You Buy At 200 With A Potential 254 Target
May 24, 2025
Apples Stock Price Should You Buy At 200 With A Potential 254 Target
May 24, 2025 -
 Frances National Rally Sundays Turnout Raises Questions About Le Pens Support
May 24, 2025
Frances National Rally Sundays Turnout Raises Questions About Le Pens Support
May 24, 2025
Latest Posts
-
 Find The Best Memorial Day 2025 Sales A Comprehensive Guide
May 24, 2025
Find The Best Memorial Day 2025 Sales A Comprehensive Guide
May 24, 2025 -
 Low Gas Prices Forecast For Memorial Day Weekend
May 24, 2025
Low Gas Prices Forecast For Memorial Day Weekend
May 24, 2025 -
 Memorial Day Weekend In Nyc A Weather Forecast
May 24, 2025
Memorial Day Weekend In Nyc A Weather Forecast
May 24, 2025 -
 Memorial Day Weekend Fueling Your Trip On The Cheap
May 24, 2025
Memorial Day Weekend Fueling Your Trip On The Cheap
May 24, 2025 -
 Best Memorial Day 2025 Sales Where To Find The Biggest Discounts
May 24, 2025
Best Memorial Day 2025 Sales Where To Find The Biggest Discounts
May 24, 2025
