Massive Office365 Data Breach Results In Millions For Hacker

Table of Contents
The Scale of the Office365 Data Breach and its Impact
This significant Office365 data breach exposed the vulnerabilities of relying solely on default security settings. The financial repercussions were staggering, serving as a potent illustration of the high cost of inadequate cybersecurity.
Financial Losses
The breach resulted in an estimated loss of several million dollars. This figure encompasses various costs:
- Ransom payments: The attackers demanded a substantial ransom for the return of stolen data.
- Legal fees: The organization incurred significant expenses in legal consultations and potential litigation.
- Remediation costs: Restoring systems, investigating the breach, and implementing new security measures added substantially to the financial burden.
- Lost revenue: Disruption to business operations during the recovery period led to significant revenue losses.
- Reputational damage: The negative publicity surrounding the breach damaged the company's reputation, potentially affecting future business opportunities and customer loyalty. In some instances, this has even led to a decline in stock prices.
Data Compromised
The scale of the data theft was equally alarming. Critically sensitive information was compromised, including:
- Personally Identifiable Information (PII): Names, addresses, email addresses, and phone numbers of numerous customers were stolen.
- Financial records: Sensitive financial data, potentially including credit card details and bank account information, was exposed.
- Intellectual property: Confidential business documents and trade secrets were among the stolen data, potentially giving competitors a significant advantage.
The exposure of this data poses serious risks to both individuals and the organization, including identity theft, financial fraud, and competitive disadvantage.
The Hacker's Methodology
The hackers employed a sophisticated multi-pronged attack. Their methods included:
- Spear phishing: Targeted emails designed to trick employees into revealing their credentials were used.
- Exploitation of known vulnerabilities: The hackers exploited known vulnerabilities in outdated software to gain unauthorized access.
- Weak password policies: The organization's lax password policy allowed the hackers to easily crack numerous user accounts.
Vulnerabilities Exposed in Office365 Security
The Office365 data breach highlighted critical vulnerabilities in the organization's security posture, revealing a reliance on default settings and a lack of essential security measures.
Weak Password Policies
Weak passwords were a significant contributing factor to the breach. Many employees used easily guessable passwords, providing an easy entry point for hackers.
- Statistics show that a significant percentage of data breaches are attributed to weak passwords.
- Implementing strong password policies, including password complexity requirements and regular password changes, is crucial.
Lack of Multi-Factor Authentication (MFA)
The absence of multi-factor authentication (MFA) significantly increased the vulnerability of the system. MFA adds an extra layer of security, making it much harder for hackers to access accounts even if they have stolen a password.
- MFA significantly reduces the risk of successful attacks.
- Studies show that MFA can reduce the risk of successful phishing attacks by up to 99%.
Unpatched Software and Vulnerabilities
Outdated software and unpatched vulnerabilities created easy entry points for the hackers. Regular software updates and security patches are essential to protect against known vulnerabilities.
- Many vulnerabilities exploited by hackers are known and have available patches.
- Regular security updates can significantly reduce the risk of successful attacks.
Lessons Learned and Best Practices for Office365 Security
The Office365 data breach provides crucial lessons for businesses. Proactive measures are essential to prevent future incidents.
Implementing Robust Security Measures
Organizations must implement robust security measures to protect their Office365 data. This includes:
- Multi-factor authentication (MFA): Implement MFA for all user accounts.
- Strong password policies: Enforce strong password policies, including password complexity, length, and regular changes.
- Regular security audits: Conduct regular security audits to identify and address vulnerabilities.
- Employee training: Invest in cybersecurity awareness training for all employees.
- Data encryption: Encrypt sensitive data both in transit and at rest.
- Intrusion detection systems: Implement intrusion detection systems to monitor for suspicious activity.
Investing in Cybersecurity Awareness Training
Employee education is critical in preventing future breaches. Training programs should cover:
- Phishing awareness
- Password security
- Safe browsing practices
- Recognizing and reporting suspicious activity
Regular Security Assessments and Penetration Testing
Proactive security measures, including regular security assessments and penetration testing, are crucial to identify vulnerabilities before they can be exploited by hackers.
- Regular assessments help identify weaknesses in security protocols.
- Penetration testing simulates real-world attacks to identify vulnerabilities.
Conclusion
The massive Office365 data breach serves as a stark reminder of the devastating consequences of inadequate cybersecurity. The millions of dollars in losses, the exposure of sensitive data, and the reputational damage highlight the critical need for robust security measures. Investing in comprehensive Office365 security, including MFA, strong password policies, regular security updates, employee training, and proactive security assessments, is no longer a luxury but a necessity for every business. Strengthen your Office365 security today and protect your business from an Office365 data breach. Learn more about securing your Office365 environment by exploring resources from Microsoft and reputable cybersecurity training providers.

Featured Posts
-
 Lizzos Powerful New Song A Return To Form
May 05, 2025
Lizzos Powerful New Song A Return To Form
May 05, 2025 -
 New Spotify Payment Methods On I Phone
May 05, 2025
New Spotify Payment Methods On I Phone
May 05, 2025 -
 Lizzo In Real Life Tour Ticket Prices A Complete Guide
May 05, 2025
Lizzo In Real Life Tour Ticket Prices A Complete Guide
May 05, 2025 -
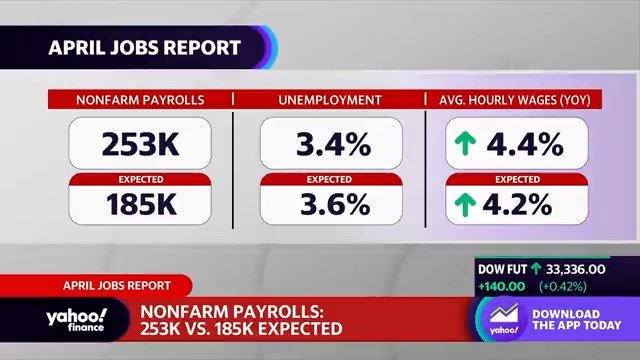 U S Jobs Report 177 000 Jobs Added In April Unemployment Remains At 4 2
May 05, 2025
U S Jobs Report 177 000 Jobs Added In April Unemployment Remains At 4 2
May 05, 2025 -
 Max Verstappen New Dad New Interview
May 05, 2025
Max Verstappen New Dad New Interview
May 05, 2025
Latest Posts
-
 Kolkata Temperature Forecast March Heatwave Warning
May 05, 2025
Kolkata Temperature Forecast March Heatwave Warning
May 05, 2025 -
 West Bengal Issues Heatwave Warning For Four Districts
May 05, 2025
West Bengal Issues Heatwave Warning For Four Districts
May 05, 2025 -
 South Bengal Heatwave Five Districts Face Extreme Heat
May 05, 2025
South Bengal Heatwave Five Districts Face Extreme Heat
May 05, 2025 -
 Heatwave Alert In West Bengal Four Districts On High Alert
May 05, 2025
Heatwave Alert In West Bengal Four Districts On High Alert
May 05, 2025 -
 Heatwave Warning 5 South Bengal Districts On High Alert
May 05, 2025
Heatwave Warning 5 South Bengal Districts On High Alert
May 05, 2025
