Major Office365 Data Breach Results In Multi-Million Dollar Theft

Table of Contents
The Scale of the Office365 Data Breach and its Financial Impact
The financial impact of data breaches is often devastating, and this recent Office365 breach is no exception. While the specific details of the affected business may not be publicly disclosed for confidentiality reasons, the reported multi-million dollar theft underscores the severity of the situation. The consequences extend far beyond the immediate financial loss.
- Quantify the financial losses: Beyond the direct loss of funds, organizations face substantial costs associated with legal fees, regulatory fines (depending on the nature of the data breached and applicable regulations like GDPR or CCPA), public relations efforts to manage reputational damage, and the cost of incident response and data recovery.
- Highlight the long-term impact: The long-term effects can include loss of customer trust, decreased market share, and difficulty securing future business partnerships. The damage to brand reputation can be particularly long-lasting.
- Mention any insurance claims or recovery efforts: The affected organization likely filed insurance claims, but the extent of coverage and the recovery process can be lengthy and complex.
Potential Vulnerabilities Exploited in the Office365 Breach
While the precise details of this particular Office365 breach might remain confidential, several common vulnerabilities could have been exploited:
- Phishing campaigns and social engineering tactics: Sophisticated phishing emails, often disguised as legitimate communications, can trick employees into revealing login credentials or clicking malicious links. These attacks often exploit social engineering techniques to manipulate users into taking actions against their better judgment.
- Weak or reused passwords: Using weak, easily guessable passwords, or reusing the same password across multiple platforms, significantly increases the risk of unauthorized access.
- Lack of Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring a second form of verification (such as a code sent to a mobile device) in addition to a password. Its absence leaves systems vulnerable.
- Unpatched software vulnerabilities in Office365 applications: Failing to update Office365 applications and operating systems regularly leaves systems open to exploitation of known security flaws. Regular patching is crucial.
- Compromised employee accounts (insider threat): Insider threats, whether malicious or unintentional, can be a significant source of data breaches. This could involve compromised accounts or employees falling victim to phishing attacks.
Best Practices for Preventing Office365 Data Breaches
Proactive security measures are crucial in preventing devastating Office365 data breaches. Implementing the following best practices can significantly mitigate your risk:
- Implement robust MFA for all user accounts: MFA is a cornerstone of modern security and should be mandatory for all users.
- Regularly update software and patches for all Office365 applications: Stay current with the latest security patches to address known vulnerabilities.
- Conduct thorough security audits and penetration testing: Regularly assess your security posture to identify weaknesses and vulnerabilities. Penetration testing simulates real-world attacks to expose potential breaches.
- Enforce strong password policies and password management strategies: Implement policies requiring strong, unique passwords and encourage the use of password managers.
- Provide comprehensive cybersecurity awareness training to employees: Educate your workforce about phishing scams, social engineering tactics, and safe internet practices.
- Utilize data loss prevention (DLP) tools: DLP tools help monitor and prevent sensitive data from leaving your organization's network.
- Implement strict access control measures based on the principle of least privilege: Grant users only the access they need to perform their jobs, limiting the potential damage from a compromised account.
The Role of Insurance and Incident Response in Mitigating Losses from Office365 Data Breaches
Proactive planning is vital in minimizing the impact of a data breach. This includes investing in cyber insurance and developing a comprehensive incident response plan.
- The benefits of having cyber liability insurance: Cyber insurance can help cover the costs of incident response, legal fees, regulatory fines, and reputational damage.
- Essential components of an effective incident response plan: A well-defined plan outlines steps to take in the event of a breach, including data breach recovery strategies.
- Steps to take immediately following a suspected breach: This includes containing the breach, investigating the cause, notifying affected parties, and collaborating with law enforcement if necessary.
- Data recovery strategies and procedures: Having a robust data backup and recovery plan in place is critical for minimizing downtime and data loss.
Conclusion
The multi-million dollar theft resulting from this Office365 data breach serves as a powerful illustration of the devastating consequences of inadequate cybersecurity. By understanding the vulnerabilities exploited and implementing the best practices outlined above, organizations can significantly reduce their risk of suffering similar attacks. Protect your business from the devastating consequences of an Office365 data breach. Implement robust security measures today and safeguard your valuable data. Learn more about securing your Office365 environment and enhancing your overall cybersecurity posture. Don't wait until it's too late; proactive Office365 security is an investment in your business's future.

Featured Posts
-
 Tghtyt Ielamyt Lqdas Alqyamt Bdyr Sydt Allwyzt Mn Alwkalt Alwtnyt Llielam
May 19, 2025
Tghtyt Ielamyt Lqdas Alqyamt Bdyr Sydt Allwyzt Mn Alwkalt Alwtnyt Llielam
May 19, 2025 -
 Art Review Modern Life A Global Artworld 1850 1950 2025
May 19, 2025
Art Review Modern Life A Global Artworld 1850 1950 2025
May 19, 2025 -
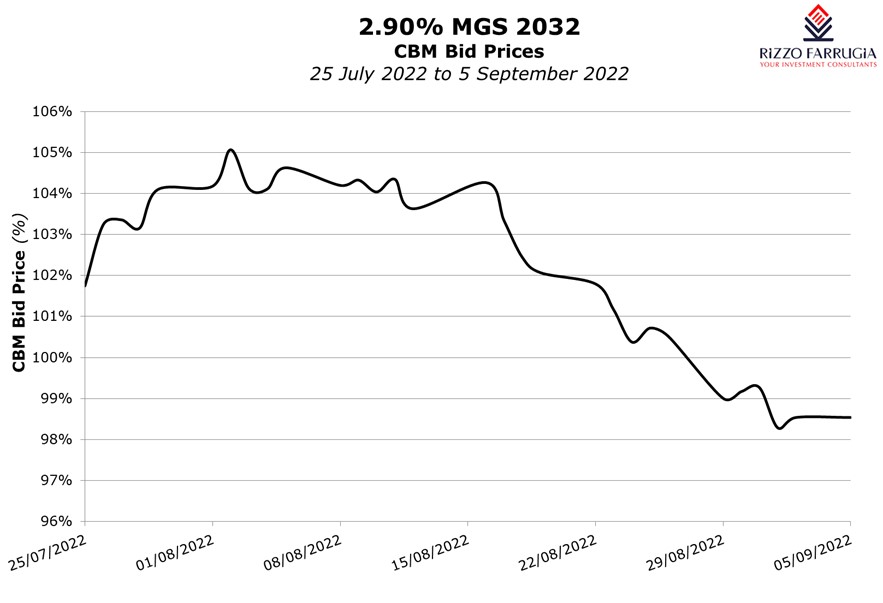 Analyzing Sovereign Bond Markets With Swissquote Bank
May 19, 2025
Analyzing Sovereign Bond Markets With Swissquote Bank
May 19, 2025 -
 Trumps Aerospace Legacy Examining The Deals And Their Outcomes
May 19, 2025
Trumps Aerospace Legacy Examining The Deals And Their Outcomes
May 19, 2025 -
 Austrias Jj Triumphs Wasted Love Wins Eurovision 2025
May 19, 2025
Austrias Jj Triumphs Wasted Love Wins Eurovision 2025
May 19, 2025
