$16 Million Fine For T-Mobile: Details On Three Years Of Data Breaches
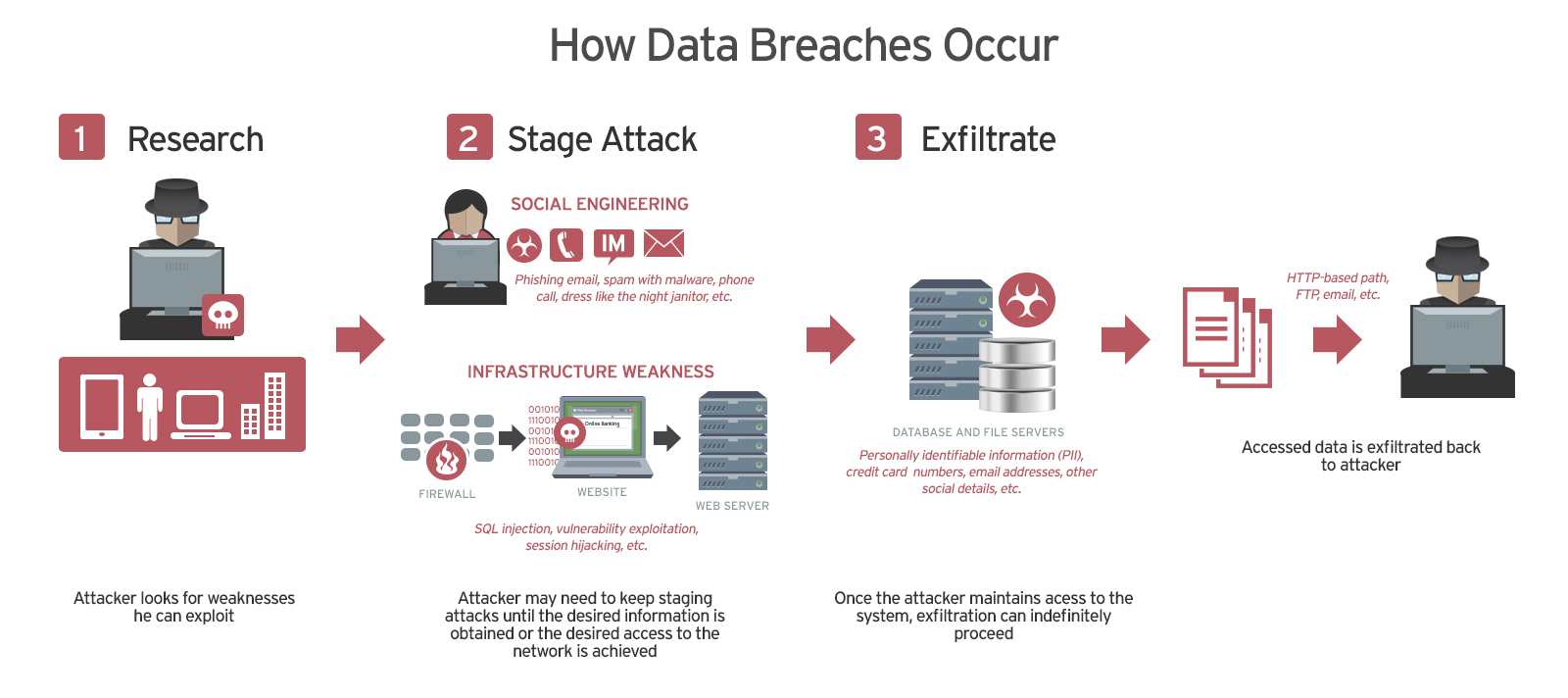
Table of Contents
T-Mobile, a leading mobile carrier, recently faced a hefty $16 million fine resulting from a series of significant data breaches spanning three years. This substantial penalty highlights the severe consequences of neglecting data security and the importance of proactive breach prevention and reporting. This article delves into the specifics of the case, outlining the violations, their impact, and the lessons learned. This case serves as a crucial example of the high cost of inadequate data security measures.
The Extent of the Data Breaches
Timeline of Events
The T-Mobile data breaches unfolded over a considerable period, exposing a significant vulnerability in their security systems. While precise dates for each individual breach aren't publicly available in full detail due to ongoing investigations, the breaches spanned at least three years, representing a significant lapse in data protection. This prolonged timeframe underscores the critical need for continuous monitoring and rapid response mechanisms to identify and mitigate security threats. Understanding the data breach timeline is crucial to comprehending the scale of the problem and the failures in T-Mobile's security protocols. This highlights the importance of a robust T-Mobile security failure response plan.
- Number of affected customers: While the exact number of affected customers in each breach remains undisclosed for each incident in its entirety, reports indicate hundreds of thousands, if not millions, were impacted over the three-year period.
- Types of data compromised: The compromised data included sensitive personal information, such as names, addresses, social security numbers, driver's license numbers, and financial details. Location data was also reportedly compromised, raising concerns about privacy violations.
- Methods used by attackers: The methods used by the attackers remain partially undisclosed for security reasons, however, it's believed that a combination of software vulnerabilities and potential network security flaws were exploited.
- Specific vulnerabilities exploited: The investigation revealed exploitation of known vulnerabilities in T-Mobile's systems, highlighting the importance of timely patching and updating of software and hardware.
Regulatory Violations and the $16 Million Fine
Specific Laws Violated
T-Mobile's failure to adequately protect customer data resulted in violations of several federal and state laws. The $16 million fine reflects penalties for non-compliance with these regulations. The specifics of which laws were violated were not all detailed publicly, however several violations are implied by the fine. The violations relate to failures in data breach notification laws, necessitating prompt reporting of incidents to affected customers and regulatory bodies. These failures illustrate the severe consequences of not adhering to GDPR and similar data protection regulations, even in cases where specific international laws may not directly apply. The FCC regulations surrounding consumer data protection were also potentially violated.
- Explanation of each violation: Each violation stems from T-Mobile's failure to implement and maintain adequate security measures, leading to the breaches and subsequent lack of timely notification to affected customers.
- Breakdown of the fine's allocation: The specific allocation of the $16 million fine among the various violations wasn't publicly detailed.
- Other penalties: In addition to the financial penalty, T-Mobile likely faced other penalties, including mandated improvements to their data security infrastructure and protocols, potentially including significant operational changes.
Impact on Consumers and T-Mobile's Reputation
Consumer Impact
The data breaches exposed millions of T-Mobile customers to significant risks. The data theft impact is multifaceted and potentially long-lasting. The consequences are far-reaching, with the potential for identity theft and significant financial loss for those affected.
- Potential risks: Consumers faced increased risks of identity theft, fraudulent credit applications, financial fraud, and other forms of identity-related crimes, as sensitive personal information was compromised.
- T-Mobile's response: T-Mobile offered credit monitoring services and other support to affected customers, although the effectiveness of these measures and the extent of information provided remains a point of contention.
- Long-term effects: The breaches have eroded customer trust and loyalty, potentially leading to customer churn and loss of market share for T-Mobile.
T-Mobile's Reputation
The breaches inflicted significant damage on T-Mobile's brand and market standing. The brand reputation damage was considerable, impacting consumer confidence and perceptions of the company's corporate responsibility. The perception of customer confidence in T-Mobile's security measures was severely affected.
- Stock market reactions: The breaches likely had a negative impact on T-Mobile's stock price, although the direct correlation is difficult to isolate.
- Public perception: Negative media coverage and public outcry further amplified the damage to T-Mobile's reputation.
- Impact on future business prospects: The breaches have negatively affected T-Mobile's ability to attract and retain customers, impacting its future growth and profitability.
Lessons Learned and Future Implications
Best Practices for Data Security
The T-Mobile case underscores the critical need for robust data security practices across all organizations handling sensitive personal information. Implementing effective data security best practices is paramount for avoiding costly and reputationally damaging breaches.
- Proactive security measures: Investing in advanced security technologies, including intrusion detection and prevention systems, is essential.
- Regular security audits: Regular security audits and penetration testing help identify vulnerabilities before attackers can exploit them.
- Employee training: Employees must receive comprehensive training on data security best practices and procedures.
- Prompt reporting: Prompt and transparent reporting of any data breaches is crucial to mitigating the damage.
Regulatory Scrutiny and Future Legislation
The T-Mobile case is likely to increase regulatory scrutiny of telecom companies and accelerate the development of stricter data privacy legislation. This will likely result in a significant change in the landscape of cybersecurity regulations and the requirements for regulatory compliance.
- Increased oversight: Expect increased regulatory oversight and enforcement of existing data protection laws.
- Stricter penalties: Future legislation may impose even stricter penalties for data breach violations, including higher fines and other sanctions.
- Evolving landscape: The evolving landscape of data security and privacy requires organizations to constantly adapt their security measures and practices.
Conclusion
The $16 million fine levied against T-Mobile serves as a stark reminder of the critical importance of robust data security measures and timely breach reporting. The breaches highlighted the significant consequences, both financially and reputationally, of failing to prioritize data protection. This case serves as a powerful example of the high costs associated with inadequate data security and the need for proactive measures.
Call to Action: Stay informed about data breach news and learn how to protect yourself from becoming a victim. Understand your rights if your data is compromised and seek further information on data security best practices to mitigate future risks associated with data breaches. Learn how to protect your personal information in the age of increasingly sophisticated cyber threats.

Featured Posts
-
 Honest Admission From Uks Eurovision Representative
Apr 25, 2025
Honest Admission From Uks Eurovision Representative
Apr 25, 2025 -
 Ubs Revises India And Hong Kong Market Forecasts
Apr 25, 2025
Ubs Revises India And Hong Kong Market Forecasts
Apr 25, 2025 -
 Crime Scene Investigation Blackbush Walk Thornaby Latest Updates
Apr 25, 2025
Crime Scene Investigation Blackbush Walk Thornaby Latest Updates
Apr 25, 2025 -
 Revolutionizing Voice Assistant Creation Open Ais 2024 Announcement
Apr 25, 2025
Revolutionizing Voice Assistant Creation Open Ais 2024 Announcement
Apr 25, 2025 -
 Dope Thief Episode 4 Ending Explained Rays Plan After Michelles Warning
Apr 25, 2025
Dope Thief Episode 4 Ending Explained Rays Plan After Michelles Warning
Apr 25, 2025
Latest Posts
-
 Post 2025 Nhl Trade Deadline A Look At Potential Playoff Matchups
May 10, 2025
Post 2025 Nhl Trade Deadline A Look At Potential Playoff Matchups
May 10, 2025 -
 Nhl Playoff Predictions Post 2025 Trade Deadline
May 10, 2025
Nhl Playoff Predictions Post 2025 Trade Deadline
May 10, 2025 -
 Nhls Hart Trophy Draisaitl Hellebuyck And Kucherov Vie For Top Honors
May 10, 2025
Nhls Hart Trophy Draisaitl Hellebuyck And Kucherov Vie For Top Honors
May 10, 2025 -
 2025 Nhl Trade Deadline Predicting The Playoff Picture
May 10, 2025
2025 Nhl Trade Deadline Predicting The Playoff Picture
May 10, 2025 -
 Hart Trophy Finalists Announced Draisaitl Hellebuyck And Kucherov
May 10, 2025
Hart Trophy Finalists Announced Draisaitl Hellebuyck And Kucherov
May 10, 2025
