Significant Office 365 Data Breach Results In Multi-Million Dollar Loss
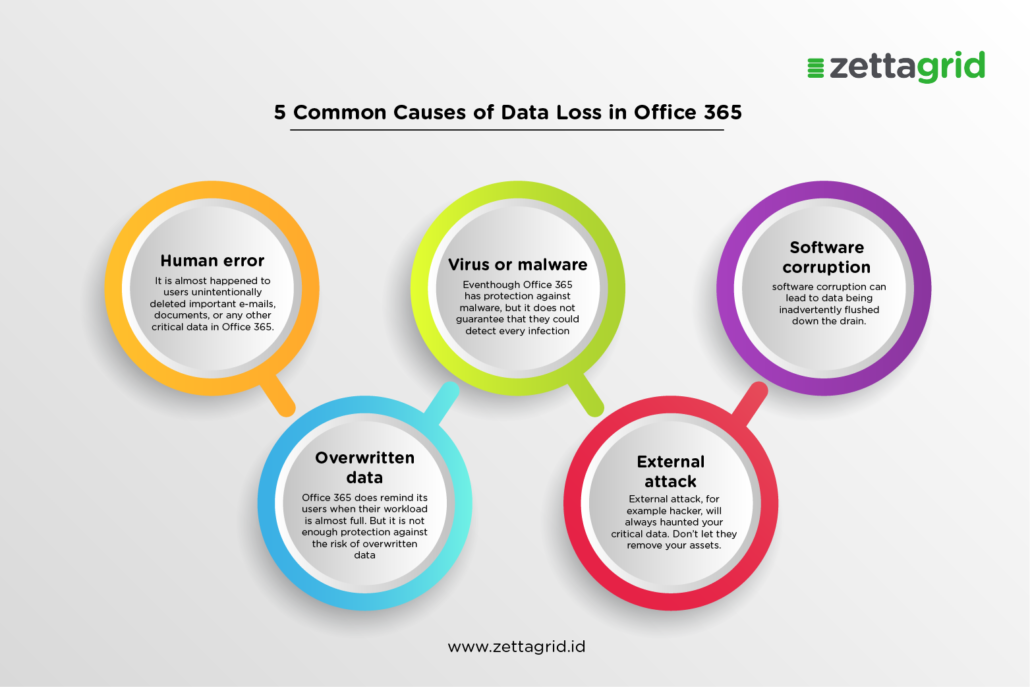
Table of Contents
The Vulnerability Landscape of Office 365
Office 365, while a powerful productivity suite, is not immune to cyberattacks. Its vast user base and interconnected nature create a tempting target for malicious actors.
Common Attack Vectors Used to Exploit Office 365 Vulnerabilities
Cybercriminals employ various methods to penetrate Office 365 security:
- Phishing and spear-phishing attacks: These deceptive emails trick employees into revealing their credentials or downloading malware. Spear-phishing targets specific individuals with personalized information, increasing its effectiveness.
- Exploiting weak or stolen passwords: Weak passwords and password reuse across multiple platforms are common entry points for hackers. Password cracking tools and credential stuffing attacks exploit these vulnerabilities.
- Compromised third-party applications: Many third-party applications integrate with Office 365. If one of these applications is compromised, it can provide a backdoor into the entire system.
- Malware infections: Malware can infect devices, granting access to Office 365 accounts and data. Ransomware attacks, in particular, are a growing threat.
- Insider threats and accidental data leaks: Negligent employees or malicious insiders can unintentionally or deliberately leak sensitive data, causing significant damage.
The Impact of Insufficient Security Measures
A lack of robust security measures significantly increases the risk of a successful Office 365 breach:
- Lack of multi-factor authentication (MFA): MFA adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain passwords.
- Failure to implement robust access controls: Properly configured access controls restrict access to sensitive data based on user roles and responsibilities.
- Inadequate employee training on cybersecurity best practices: Employees are often the weakest link in security. Regular training is essential to raise awareness and improve security practices.
- Absence of regular security audits and vulnerability assessments: Regular audits identify vulnerabilities and weaknesses before attackers can exploit them.
Specific Examples of Successful Office 365 Breaches and Their Methods
While many breaches remain undisclosed for confidentiality reasons, publicly reported incidents illustrate the real-world consequences. For instance, [insert a real-world example of an Office 365 breach and its method, citing a reputable source]. This highlights the importance of proactive security measures.
The Financial Ramifications of a Major Office 365 Data Breach
The financial impact of a significant Office 365 data breach can be catastrophic, encompassing both direct and indirect costs.
Direct Costs Associated with a Breach
- Incident response costs: These include forensic investigation, legal fees, and public relations efforts to manage the fallout.
- Data recovery and restoration costs: Recovering and restoring compromised data can be a lengthy and expensive process.
- Notification costs: Organizations are legally obligated to notify affected individuals and regulatory bodies, which incurs significant costs.
Indirect Costs Resulting from a Breach
- Loss of customer trust and reputation damage: A data breach severely erodes customer trust, leading to lost business and revenue.
- Decreased productivity and operational disruption: Responding to a breach and recovering from its effects disrupts operations and reduces productivity.
- Potential fines and penalties from regulatory bodies: Non-compliance with regulations like GDPR and CCPA can result in substantial fines.
- Loss of business opportunities and contracts: Damaged reputation can lead to lost business opportunities and the termination of contracts.
Illustrative Example of a Multi-Million Dollar Loss Scenario
Imagine a company with 10,000 employees experiencing a significant Office 365 data breach exposing customer data. The incident response, legal fees, regulatory fines, loss of customers, and reputational damage could easily result in a multi-million dollar loss, potentially exceeding $5 million or more depending on the severity and nature of the data compromised.
Mitigating the Risk of a Significant Office 365 Data Breach
Proactive measures are crucial in preventing a devastating Office 365 data breach.
Implementing Robust Security Measures
- Enforce multi-factor authentication (MFA) for all users: MFA is a fundamental security measure that should be mandatory for all accounts.
- Regularly update software and patches: Keeping software up-to-date patches vulnerabilities that attackers could exploit.
- Implement strong password policies and promote password management best practices: Strong, unique passwords and password managers significantly improve security.
- Employ advanced threat protection solutions: These solutions leverage advanced technologies to detect and prevent sophisticated attacks.
- Utilize data loss prevention (DLP) tools: DLP tools monitor and prevent sensitive data from leaving the organization's control.
- Conduct regular security awareness training for employees: Training empowers employees to identify and avoid phishing attempts and other social engineering attacks.
Employing a Layered Security Approach to Enhance Protection Against Various Attack Vectors
A layered security approach combines multiple security controls to provide comprehensive protection. This includes technical controls like firewalls and intrusion detection systems, along with procedural safeguards such as access control policies and incident response plans. Continuous monitoring and logging are crucial for early detection of threats.
Leveraging Office 365's Built-in Security Features
Office 365 offers several built-in security features that should be fully utilized:
- Advanced Threat Protection: This feature provides enhanced protection against phishing attacks and malware.
- Information Protection: This allows for the classification and protection of sensitive information.
- Access Management: This feature allows for granular control over user access to data and resources.
Conclusion: Protecting Your Business from Significant Office 365 Data Breaches
A significant Office 365 data breach can have severe financial and reputational consequences, resulting in multi-million dollar losses and long-term damage. Proactive security measures, including robust authentication, regular updates, employee training, and the use of advanced threat protection solutions, are essential to mitigate this risk. Don't wait for a breach to occur; invest in robust Office 365 security solutions and implement best practices to protect your data and your business. Contact us today to learn more about securing your Office 365 environment and preventing a devastating Office 365 data breach. [Insert links to relevant resources or services here].

Featured Posts
-
 Cobra Kais Continuity How The Show Expands The Karate Kid Universe
May 23, 2025
Cobra Kais Continuity How The Show Expands The Karate Kid Universe
May 23, 2025 -
 How Alix Earle Conquered Gen Z As Dancing With The Stars Newest Marketing Maven
May 23, 2025
How Alix Earle Conquered Gen Z As Dancing With The Stars Newest Marketing Maven
May 23, 2025 -
 Macaulay Culkin And Kieran Culkin Mothers Alleged Financial Hardship Despite Sons Wealth
May 23, 2025
Macaulay Culkin And Kieran Culkin Mothers Alleged Financial Hardship Despite Sons Wealth
May 23, 2025 -
 Mutlq Alnar Ela Mwzfy Sfart Alahtlal Srkhat Alhryt Lflstyn
May 23, 2025
Mutlq Alnar Ela Mwzfy Sfart Alahtlal Srkhat Alhryt Lflstyn
May 23, 2025 -
 Freepoint Eco Systems And Ing Announce Major Project Finance Deal
May 23, 2025
Freepoint Eco Systems And Ing Announce Major Project Finance Deal
May 23, 2025
Latest Posts
-
 The Last Rodeo Examining Neal Mc Donoughs Character
May 23, 2025
The Last Rodeo Examining Neal Mc Donoughs Character
May 23, 2025 -
 Neal Mc Donoughs Role In The Last Rodeo
May 23, 2025
Neal Mc Donoughs Role In The Last Rodeo
May 23, 2025 -
 Smart Shopping For Memorial Day 2025 Best Sales And Deals
May 23, 2025
Smart Shopping For Memorial Day 2025 Best Sales And Deals
May 23, 2025 -
 Dallas Welcomes The Usa Film Festival Free Movies And Star Guests
May 23, 2025
Dallas Welcomes The Usa Film Festival Free Movies And Star Guests
May 23, 2025 -
 Dc Legends Of Tomorrow The Ultimate Fans Resource
May 23, 2025
Dc Legends Of Tomorrow The Ultimate Fans Resource
May 23, 2025
