Post-Quantum Cryptography Market To Reach Billions By 2030: Impact Of New Algorithm Standards And Migration Timelines
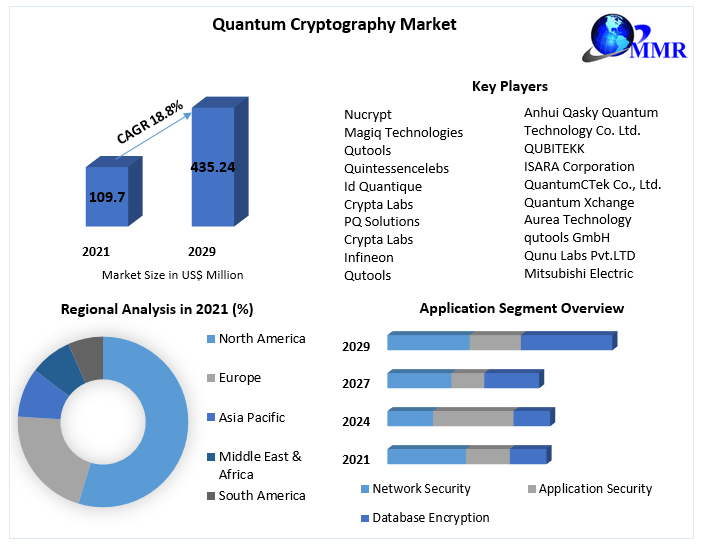
Table of Contents
The Rising Threat of Quantum Computing and the Need for Post-Quantum Cryptography
Vulnerability of Current Encryption Algorithms
Quantum computers leverage the principles of quantum mechanics to perform calculations far beyond the capabilities of classical computers. This immense processing power poses a direct threat to the widely used public-key cryptography algorithms that underpin much of our digital security. Algorithms like RSA and Elliptic Curve Cryptography (ECC), currently used to secure online transactions, communications, and data storage, are vulnerable to attacks from sufficiently powerful quantum computers.
- Specific examples of vulnerable algorithms: RSA, ECC, DSA (Digital Signature Algorithm).
- Potential impact: Data breaches on a massive scale, compromise of sensitive information (financial data, personal records, national security secrets), and disruption of critical infrastructure.
- Statistics: Predictions vary, but experts anticipate that powerful quantum computers capable of breaking current encryption will be available within the next decade or two. The rapid advancement of quantum computing technology underscores the urgency of the situation.
Post-Quantum Cryptography as a Solution
Post-quantum cryptography (PQC), also known as quantum-resistant cryptography, encompasses cryptographic algorithms designed to withstand attacks from both classical and quantum computers. Transitioning to PQC is not merely a future consideration; it's a critical step in ensuring long-term data security.
- Different types of PQC algorithms:
- Lattice-based cryptography: Relies on the hardness of lattice problems in high-dimensional spaces. Examples include CRYSTALS-Kyber and CRYSTALS-Dilithium.
- Code-based cryptography: Based on the difficulty of decoding certain types of error-correcting codes. An example is Classic McEliece.
- Multivariate cryptography: Uses the difficulty of solving systems of multivariate polynomial equations. An example is Rainbow.
- Hash-based cryptography: Relies on the cryptographic hash function. An example is SPHINCS+.
- Advantages and disadvantages: Each type offers unique strengths and weaknesses in terms of performance, security, and key size. The choice of algorithm will depend on specific security requirements and implementation constraints.
Impact of New Algorithm Standards on the Post-Quantum Cryptography Market
NIST's Standardization Efforts
The National Institute of Standards and Technology (NIST) has played a crucial role in driving the adoption of PQC through its standardization process. This rigorous process has resulted in the selection of several quantum-resistant algorithms for various cryptographic tasks. This standardization is vital in fostering interoperability and accelerating the migration to PQC.
- Selected algorithms and key features: NIST has selected several algorithms, including CRYSTALS-Kyber (key establishment), CRYSTALS-Dilithium (digital signatures), FALCON (digital signatures), SPHINCS+ (digital signatures), and Classic McEliece (key establishment). Each algorithm offers specific advantages concerning security, performance, and key size.
- Timeline for implementation and adoption: NIST has published standards, and the implementation process is ongoing. The timeline for full adoption varies across industries and applications.
- Implications for different industries: The impact of PQC standardization will be felt across various sectors, requiring adaptation of existing systems and the development of new security protocols.
Market Response to Standardization
The market is responding positively to NIST's standardization efforts. Several vendors are already integrating PQC solutions into their products, leading to increased investment and product development in the quantum-resistant cryptography space.
- Examples of companies offering PQC solutions: Many cybersecurity companies are actively developing and deploying PQC solutions. This includes both established players and new entrants in the market.
- Emerging market trends and opportunities: The market is witnessing a surge in demand for PQC solutions, creating opportunities for innovation and partnerships.
- Role of open-source initiatives: Open-source projects are contributing significantly to the development and dissemination of PQC algorithms and related tools.
Migration Timelines and Challenges in Implementing Post-Quantum Cryptography
Complexity of Migration
Migrating existing systems to PQC is a complex undertaking, requiring careful planning and phased implementation. The process involves significant technical and logistical challenges.
- Potential compatibility issues: Integrating PQC into legacy systems can present compatibility problems and require significant software updates or replacements.
- Need for skilled professionals and training: Specialized expertise is needed for the design, implementation, and management of PQC systems. Training and development programs are crucial.
- Cost implications of migration: The cost of migration can be substantial, encompassing software upgrades, system testing, and employee training.
Strategies for Successful Migration
Organizations need a well-defined strategy to successfully migrate to PQC. This involves a comprehensive assessment of their risk exposure, a phased deployment approach, and ongoing monitoring of system security.
- Actionable steps for organizations: Begin by assessing current cryptographic infrastructure, identify critical systems, and prioritize migration efforts based on risk levels. Select appropriate PQC algorithms and develop a comprehensive implementation plan.
- Importance of collaboration and industry partnerships: Collaboration within organizations and industry partnerships can significantly facilitate the migration process and share best practices.
Conclusion
The threat of quantum computing is real, and the need for post-quantum cryptography is undeniable. The post-quantum cryptography market, driven by NIST standardization and increasing awareness of the quantum threat, is poised for substantial growth, projected to reach billions by 2030. Successfully navigating the complexities of algorithm standardization and migration timelines is paramount for organizations to ensure the long-term security of their data. Don't wait until it's too late: Prepare your organization for the quantum era with post-quantum cryptography today. Learn more by exploring resources from NIST and industry leaders in quantum-resistant cryptography.

Featured Posts
-
 Dzherard Btlr I Blgariya Nezabravimi Momenti
May 13, 2025
Dzherard Btlr I Blgariya Nezabravimi Momenti
May 13, 2025 -
 Stuttgart Open Ostapenko Defeats Swiatek For Second Time Reaches Semis
May 13, 2025
Stuttgart Open Ostapenko Defeats Swiatek For Second Time Reaches Semis
May 13, 2025 -
 Case Study Addendum Byds Leadership In Ev Battery Manufacturing
May 13, 2025
Case Study Addendum Byds Leadership In Ev Battery Manufacturing
May 13, 2025 -
 Update Search Continues For Missing Elderly Hiker In Peninsula Hills
May 13, 2025
Update Search Continues For Missing Elderly Hiker In Peninsula Hills
May 13, 2025 -
 Noida And Ghaziabad Heatwave Warning Advisory For Outdoor Workers
May 13, 2025
Noida And Ghaziabad Heatwave Warning Advisory For Outdoor Workers
May 13, 2025
