Office365 Security Failure Leads To Millions In Losses For Executives
Table of Contents
Common Office365 Vulnerabilities Exploited by Cybercriminals
Cybercriminals employ various tactics to exploit vulnerabilities in Office365, leading to costly Office365 security failures. Understanding these vulnerabilities is the first step towards robust protection.
Phishing and Social Engineering Attacks
Phishing emails and social engineering attacks exploit human error to gain access to Office365 accounts. These attacks often involve cleverly crafted emails mimicking legitimate organizations, urging users to click malicious links or reveal sensitive information like passwords.
- Examples: Emails pretending to be from Microsoft, requesting password resets or claiming account suspension.
- Consequences:
- Data breaches exposing sensitive customer information.
- Ransomware attacks encrypting critical files and demanding payment.
- Financial loss through fraudulent transactions.
Weak or Shared Passwords
Using weak or shared passwords significantly increases the risk of an Office365 security failure. Weak passwords are easily guessed, while shared passwords expose the entire organization to risk if one account is compromised.
- Dangers: Simple passwords, password reuse across multiple platforms, and lack of password complexity.
- Importance of Strong Passwords: Strong, unique passwords, ideally generated by password managers, are essential. Password complexity should include uppercase and lowercase letters, numbers, and symbols.
- Impact: Easy access for cybercriminals, leading to data theft, account hijacking, and potentially malware infections.
Unpatched Software and Outdated Systems
Failing to update Office365 software and neglecting security updates creates critical vulnerabilities that cybercriminals exploit. Outdated systems lack the latest security patches, making them easy targets for attacks.
- Security Risks: Unpatched software contains known vulnerabilities that can be leveraged by malicious actors.
- Importance of Regular Updates: Regularly updating Office365 software and operating systems is crucial to mitigate these risks. Enable automatic updates wherever possible.
- Consequences: Exposure to malware, data breaches, and system instability.
Lack of Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) significantly enhances Office365 security by adding an extra layer of protection beyond just a password.
- Critical Role of MFA: Even if a password is compromised, MFA prevents unauthorized access by requiring a second verification method.
- Types of MFA: Common methods include one-time codes sent via text message, authenticator apps, or security keys.
- Prevention of Unauthorized Access: MFA effectively blocks access even if credentials are stolen, drastically reducing the risk of an Office365 security failure.
The Financial Ramifications of Office365 Security Breaches for Executives
The financial consequences of Office365 security failures can be catastrophic for businesses and devastating for executives.
Direct Financial Losses
Data breaches associated with Office365 security failures result in substantial direct financial losses.
- Costs: Legal fees, regulatory fines (like GDPR penalties), incident response costs, and recovery efforts.
- Real-world Scenarios: Many large companies have suffered millions in losses due to Office365 breaches.
- Financial Repercussions: Loss of revenue, damaged equipment, and significant operational downtime.
Reputational Damage and Loss of Customer Trust
Data breaches severely damage a company's reputation and erode customer trust.
- Negative Impact: Loss of customers, reduced sales, and difficulty attracting new business.
- Long-term Consequences: Reputational damage can have long-lasting and far-reaching financial repercussions.
- Loss of Customers and Revenue: Customers may switch to competitors perceived as more secure.
Impact on Shareholder Value and Executive Compensation
Office365 security failures can significantly impact shareholder value and potentially lead to legal action and career repercussions for executives.
- Impact on Stock Price: A major breach can cause a dramatic drop in stock price.
- Executive Consequences: Executives may face lawsuits, reputational damage, and even job loss.
- Potential for Legal Action: Shareholders may sue for negligence in protecting company assets.
Proactive Strategies to Prevent Office365 Security Failures
Implementing proactive strategies is critical to prevent costly Office365 security failures.
Implementing Robust Security Policies and Procedures
Establishing and enforcing comprehensive security policies is essential.
- Importance of Strong Policies: Clear guidelines on password management, acceptable use, and data handling.
- Best Practices: Regular security awareness training, incident response plans, and multi-factor authentication.
- Key Aspects: Access control, data encryption, and regular security assessments.
Utilizing Advanced Security Features within Office365
Office365 offers advanced security features to enhance protection.
- Advanced Threat Protection: Detects and blocks malicious emails and attachments.
- Data Loss Prevention (DLP): Prevents sensitive data from leaving the organization.
- Information Protection: Controls access to and usage of sensitive information.
Regular Security Audits and Penetration Testing
Regular security assessments identify vulnerabilities before they can be exploited.
- Importance of Audits: Identifying weaknesses in security posture and recommending improvements.
- Benefits of Penetration Testing: Simulates real-world attacks to identify exploitable vulnerabilities.
- Steps in a Security Audit: Vulnerability scanning, risk assessment, and remediation planning.
Employee Security Awareness Training
Educating employees about security threats is crucial.
- Critical Role of Training: Empowering employees to identify and report phishing attempts and other threats.
- Effective Training Programs: Regular training sessions, phishing simulations, and clear communication of security policies.
- Essential Topics: Password security, phishing awareness, social engineering tactics, and safe browsing practices.
Conclusion: Protecting Your Business from Office365 Security Failures
The high cost of Office365 security failures, including direct financial losses, reputational damage, and legal repercussions, cannot be overstated. Implementing robust security policies, utilizing Office365's advanced security features, conducting regular security audits, and investing in comprehensive employee training are vital to protecting your business. Strengthen your Office365 security today and prevent costly Office365 security breaches. Invest in robust Office365 security solutions to safeguard your organization's future.

Featured Posts
-
 The Mindy Project And The Office Exploring Mindy Kaling And B J Novaks On Screen And Off Screen Chemistry
May 06, 2025
The Mindy Project And The Office Exploring Mindy Kaling And B J Novaks On Screen And Off Screen Chemistry
May 06, 2025 -
 Mindy Kaling And B J Novak Friendship A Response To Recent Relationship Rumors
May 06, 2025
Mindy Kaling And B J Novak Friendship A Response To Recent Relationship Rumors
May 06, 2025 -
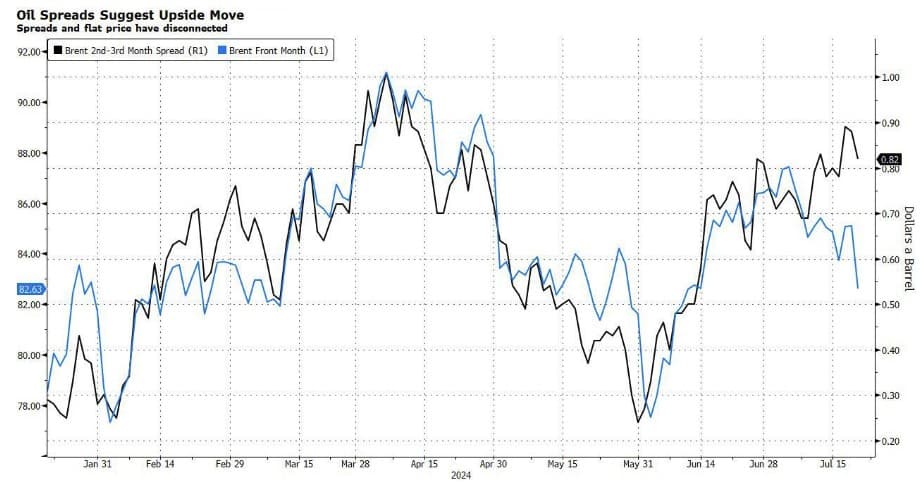 Australian Election Potential Market Upswing For Assets
May 06, 2025
Australian Election Potential Market Upswing For Assets
May 06, 2025 -
 Rising Waters Threaten Venice Exploring A Bold New Solution
May 06, 2025
Rising Waters Threaten Venice Exploring A Bold New Solution
May 06, 2025 -
 Five Key Charts To Watch In Global Commodity Markets This Week
May 06, 2025
Five Key Charts To Watch In Global Commodity Markets This Week
May 06, 2025
Latest Posts
-
 Duze Zamowienie Trotylu Polska Na Swiatowym Rynku Materialow Wybuchowych
May 06, 2025
Duze Zamowienie Trotylu Polska Na Swiatowym Rynku Materialow Wybuchowych
May 06, 2025 -
 Polska I Eksport Trotylu Rzut Oka Na Duze Zamowienie
May 06, 2025
Polska I Eksport Trotylu Rzut Oka Na Duze Zamowienie
May 06, 2025 -
 Zamowienie Na Trotyl Z Polski Implikacje Dla Bezpieczenstwa
May 06, 2025
Zamowienie Na Trotyl Z Polski Implikacje Dla Bezpieczenstwa
May 06, 2025 -
 Analyzing The Popularity Of Leon Thomas And Halle Baileys Rather Be Alone
May 06, 2025
Analyzing The Popularity Of Leon Thomas And Halle Baileys Rather Be Alone
May 06, 2025 -
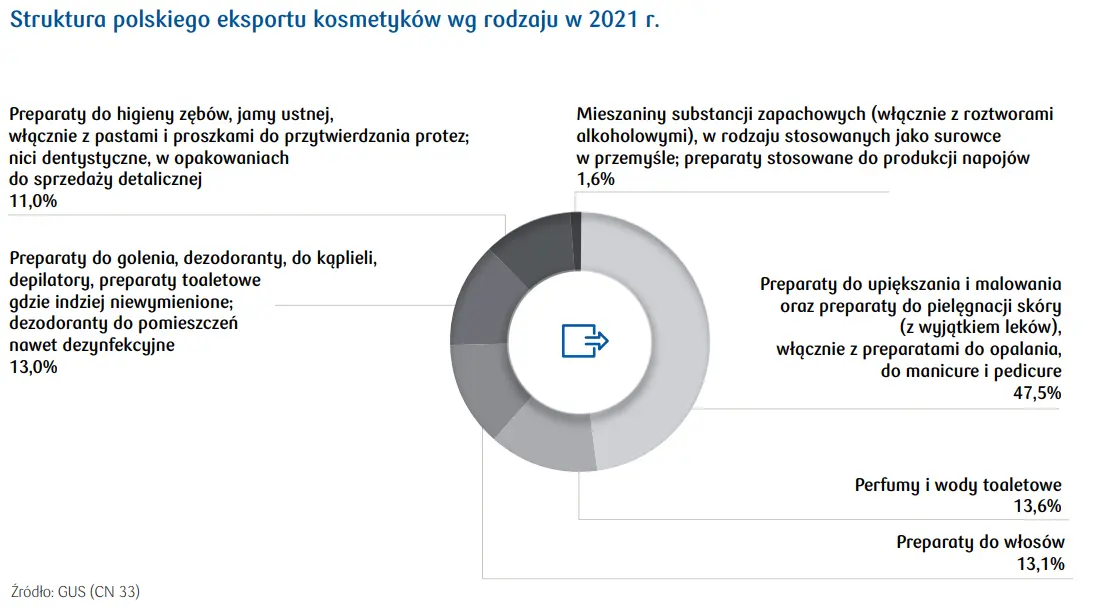 Kontrowersyjny Eksport Trotylu Z Polski Analiza Zamowienia
May 06, 2025
Kontrowersyjny Eksport Trotylu Z Polski Analiza Zamowienia
May 06, 2025
