Office365 Executive Inbox Compromise Results In Multi-Million Dollar Loss
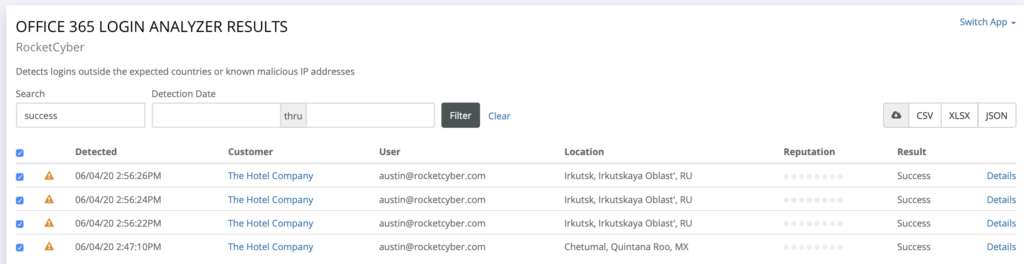
Table of Contents
Understanding the Office365 Executive Inbox Compromise Threat
The Mechanics of an Attack
Cybercriminals employ various sophisticated techniques to gain access to executive inboxes. These attacks often exploit vulnerabilities within the Office365 ecosystem, focusing on human error and weak security practices. Common attack vectors include:
- Phishing Emails: These emails often mimic legitimate communications from trusted sources, urging recipients to click malicious links or download infected attachments. They might appear to be from banks, clients, or even internal colleagues.
- Spear-Phishing: More targeted than general phishing, spear-phishing attacks leverage personalized information about the executive to increase their effectiveness. These emails often contain details gleaned from social media or other public sources.
- Credential Stuffing: Attackers use stolen usernames and passwords obtained from other data breaches to attempt to access Office365 accounts. They leverage lists of compromised credentials and systematically try them against various platforms, including Office365.
- Exploiting Third-Party App Vulnerabilities: Many organizations integrate third-party applications with Office365. If these apps have security flaws, attackers can exploit them to gain unauthorized access to executive inboxes.
Why Executives Are Prime Targets
Executives are high-value targets for cybercriminals due to their access to sensitive information and authority within an organization. Compromising an executive account grants attackers significant leverage:
- Access to Financial Systems: Executives often have the authority to initiate wire transfers, approve payments, and access critical financial data.
- Authority to Approve Large Transactions: Fraudsters can leverage compromised accounts to authorize fraudulent payments or divert funds to their own accounts.
- Control over Company Strategy and Sensitive Information: Access to an executive inbox provides valuable intelligence, potentially enabling corporate espionage, intellectual property theft, or sabotage.
The Financial Ramifications of a Successful Compromise
Direct Financial Losses
A successful Office365 executive inbox compromise can result in significant direct financial losses, including:
- Unauthorized Wire Transfers: Attackers can initiate fraudulent wire transfers to overseas accounts, often leaving little trace.
- Payment of Fake Invoices: Cybercriminals can send seemingly legitimate invoices that mimic real business transactions, deceiving executives into paying fraudulent bills.
- Ransom Demands: Following a successful breach, attackers might encrypt sensitive data and demand a ransom for its release. The financial impact can be catastrophic, particularly for larger organizations.
Indirect Costs
Beyond direct financial losses, a successful attack can incur substantial indirect costs:
- Reputational Damage: A security breach can severely damage an organization's reputation, leading to a loss of customer trust and investor confidence.
- Legal Fees and Regulatory Fines: Organizations may face costly legal battles and significant fines from regulatory bodies for failing to protect sensitive data.
- Incident Response and Recovery Costs: The process of investigating, containing, and remediating a security breach requires significant resources, time, and expertise.
- Business Disruption and Loss of Productivity: A security incident can disrupt business operations, impacting productivity and potentially causing lost revenue.
Implementing Robust Security Measures to Prevent Office365 Executive Inbox Compromises
Multi-Factor Authentication (MFA)
Implementing robust MFA is crucial for enhancing the security of executive accounts. MFA adds an extra layer of security, requiring users to provide multiple forms of authentication to access their accounts. This significantly reduces the risk of unauthorized access, even if credentials are compromised:
- Authenticator Apps: Use authenticator apps like Google Authenticator or Microsoft Authenticator to generate time-based one-time passwords.
- Hardware Security Keys: Hardware security keys provide a more secure and tamper-resistant form of MFA.
- One-Time Passwords (OTPs): Receive OTPs via SMS or email to verify your identity.
Advanced Threat Protection (ATP)
Microsoft's Advanced Threat Protection (ATP), and similar solutions from other vendors, offer robust protection against sophisticated threats. Key features include:
- Real-Time Protection: ATP actively scans emails and attachments for malicious content, blocking threats before they reach your inbox.
- Anti-Spoofing Measures: ATP helps to identify and block email messages that attempt to impersonate legitimate senders, mitigating the risk of phishing attacks.
- Sandbox Analysis: Suspect files are analyzed in a secure sandbox environment to detect malicious behavior without exposing your systems to risk.
Security Awareness Training
Investing in comprehensive security awareness training is essential, particularly for executives. This training should focus on recognizing and reporting phishing attempts and understanding social engineering tactics:
- Regular Training Sessions: Conduct regular training sessions to reinforce best practices and keep employees up-to-date on the latest threats.
- Phishing Simulations: Conduct simulated phishing attacks to test employee awareness and identify vulnerabilities.
- Clear Guidelines: Provide clear guidelines on how to identify and handle suspicious emails.
Access Control and Privilege Management
Implementing the principle of least privilege is vital. This ensures that users only have access to the data and systems they need to perform their jobs:
- Regular Permission Reviews: Regularly review and update user permissions to ensure they remain appropriate.
- Role-Based Access Control (RBAC): Implement RBAC to assign permissions based on user roles and responsibilities.
- User Activity Monitoring: Monitor user activity for suspicious behavior, such as unusual login attempts or access to sensitive data.
Conclusion: Protecting Your Organization from Office365 Executive Inbox Compromises
Office365 executive inbox compromises pose a significant threat to organizations of all sizes, leading to devastating financial and reputational consequences. Implementing a multi-layered security approach that combines robust MFA, advanced threat protection, comprehensive security awareness training, and effective access control is crucial. By proactively investing in these security measures, you can significantly reduce your risk of falling victim to these attacks and protect your organization from potentially multi-million dollar losses. Secure your Office365 environment today. Invest in robust Office365 security solutions and strengthen your defenses against Office365 executive email compromises now.

Featured Posts
-
 Kivalliq Hydro Fibre Link A New Energy And Economic Corridor For Manitoba And Nunavut
May 30, 2025
Kivalliq Hydro Fibre Link A New Energy And Economic Corridor For Manitoba And Nunavut
May 30, 2025 -
 Anomalnaya Zhara Zatem Pokholodanie I Silniy Shtorm Preduprezhdenie Mada Dlya Izrailya
May 30, 2025
Anomalnaya Zhara Zatem Pokholodanie I Silniy Shtorm Preduprezhdenie Mada Dlya Izrailya
May 30, 2025 -
 Kasper Dolberg London Klubs Viser Interesse
May 30, 2025
Kasper Dolberg London Klubs Viser Interesse
May 30, 2025 -
 A69 Le Gouvernement Tente De Relancer Les Travaux Apres Annulation
May 30, 2025
A69 Le Gouvernement Tente De Relancer Les Travaux Apres Annulation
May 30, 2025 -
 Des Moines Memorial Day Weekend Events Parades And Remembrance
May 30, 2025
Des Moines Memorial Day Weekend Events Parades And Remembrance
May 30, 2025
