Execs' Office365 Accounts Breached: Crook Makes Millions, Feds Say
Table of Contents
The Scale of the Office365 Breach and its Impact
The recent Office365 security breach exposed the vulnerability of executive accounts to sophisticated cyberattacks, resulting in significant financial losses and reputational damage. The scale of the breach is staggering, underscoring the urgent need for improved cybersecurity practices across all industries.
- Number of executive accounts compromised: While the exact number remains undisclosed for security reasons, reports suggest that dozens of high-level executive accounts across multiple companies were compromised. This highlights the broad reach and effectiveness of the attackers’ methods.
- Total financial losses attributed to the breach: Federal investigators estimate that the cybercriminal operation netted millions of dollars through fraudulent wire transfers and other illicit activities facilitated by access to compromised email accounts.
- Types of data stolen: The stolen data included sensitive financial records, confidential company information, strategic plans, and intellectual property. The impact extends far beyond immediate financial losses, potentially compromising long-term business strategies and competitive advantage.
- Industries affected: The breach affected companies across various sectors, including finance, technology, and manufacturing. This demonstrates that no industry is immune to these types of sophisticated cyberattacks. The lack of industry specificity underscores the pervasiveness of the threat.
- Long-term implications: The long-term implications for affected companies include legal ramifications, reputational damage, loss of investor confidence, and the potential for further exploitation of compromised data. For individuals, the consequences can include identity theft and financial ruin.
Methods Used in the Office365 Breach: Sophisticated Phishing and Beyond
The criminals behind this Office365 breach employed highly sophisticated techniques to bypass security measures and gain access to executive accounts. This wasn't a simple phishing scam; it was a carefully orchestrated attack leveraging multiple vectors.
- Spear phishing: The attackers used spear phishing, crafting highly targeted emails designed to look legitimate and enticing to specific executives. These emails often contained urgent requests or seemingly innocuous attachments designed to deliver malware or harvest credentials.
- Malware and malicious software: Once initial access was gained, the criminals likely deployed malware to maintain persistent access, steal data, and potentially enable further attacks within the network.
- Multi-factor authentication bypass: The ability of the criminals to bypass multi-factor authentication (MFA) suggests either a sophisticated attack exploiting vulnerabilities in the MFA system or a compromise of secondary authentication factors. This highlights the need for robust and well-implemented MFA solutions.
- Social engineering: The success of the attack also points to effective social engineering techniques used to manipulate executives into divulging sensitive information or clicking on malicious links. The attackers likely used a combination of urgency and trust to gain their victims' cooperation.
The Role of Weak Security Practices and Lack of Awareness
While the criminals used sophisticated methods, the success of this Office365 breach also highlights the role of weak security practices and a lack of awareness among employees.
- Security weaknesses exploited: The breach exposed weaknesses in password security, lack of consistent multi-factor authentication (MFA) enforcement, and insufficient security awareness training.
- Importance of strong passwords and MFA: Strong, unique passwords and the mandatory use of MFA are critical in preventing unauthorized access. Weak passwords and a lack of MFA were clearly major contributing factors in this breach.
- Security awareness training: Comprehensive security awareness training for all employees is paramount to reduce the risk of phishing attacks and other social engineering tactics. Employees need to be educated to recognize and report suspicious emails and attachments.
- Regular security audits and updates: Regular security audits and timely updates for Office365 are essential for maintaining a secure environment and patching known vulnerabilities. Ignoring these crucial steps leaves organizations vulnerable to exploitation.
Protecting Your Organization from Similar Office365 Breaches
Preventing similar Office365 breaches requires a multi-layered approach to cybersecurity, combining technological solutions with a strong emphasis on employee education and proactive threat intelligence.
- Improving Office365 security: Implement strong password policies, enforce multi-factor authentication (MFA) for all accounts, and regularly update Office365 software and security settings. Leverage advanced threat protection features offered by Microsoft.
- Threat intelligence: Stay informed about emerging cyber threats and vulnerabilities through threat intelligence feeds and security advisories. This helps proactively identify and address potential risks.
- Incident response plan: Develop and regularly test a comprehensive incident response plan to quickly contain and mitigate the impact of any security breach. This includes clear procedures for identifying, responding to, and recovering from an attack.
- Data loss prevention (DLP): Implement data loss prevention (DLP) tools to monitor and control the movement of sensitive data within your organization, reducing the risk of data exfiltration in the event of a breach.
Conclusion
The recent Office365 breach, resulting in millions of dollars in losses, underscores the critical importance of robust cybersecurity practices. The sophisticated methods employed highlight the need for proactive security measures, including strong password policies, mandatory multi-factor authentication, comprehensive security awareness training, and a well-defined incident response plan. The attackers successfully exploited weaknesses in security practices and a lack of awareness, demonstrating that even the most secure-seeming systems are vulnerable without a holistic approach to security. Don't let your organization become the next victim of an Office365 breach. Implement strong security measures, provide comprehensive security awareness training, and stay vigilant against evolving cyber threats. Protect your valuable data and financial assets by prioritizing Office365 security today.

Featured Posts
-
 Ftc V Meta The Latest Updates On Instagram And Whats App
Apr 30, 2025
Ftc V Meta The Latest Updates On Instagram And Whats App
Apr 30, 2025 -
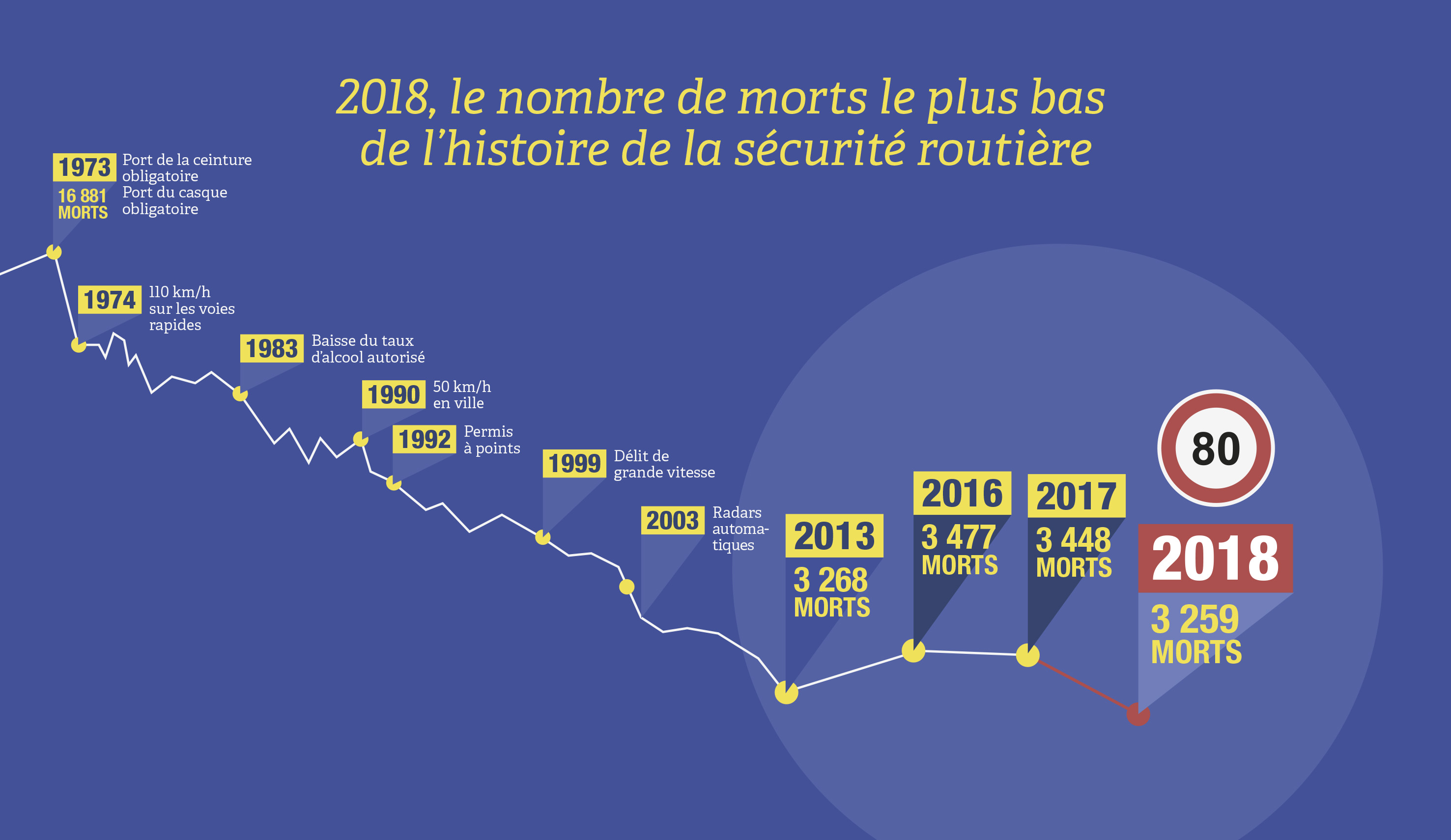 Glissieres De Securite Impact Sur La Mortalite Routiere
Apr 30, 2025
Glissieres De Securite Impact Sur La Mortalite Routiere
Apr 30, 2025 -
 Disneys Alaska 2026 Two Cruise Ships Set Sail
Apr 30, 2025
Disneys Alaska 2026 Two Cruise Ships Set Sail
Apr 30, 2025 -
 Papa Francesco E Cardinale Becciu Le Dimissioni Sono Premature
Apr 30, 2025
Papa Francesco E Cardinale Becciu Le Dimissioni Sono Premature
Apr 30, 2025 -
 Could Gillian Anderson Reprise Her Role In A New X Files Series
Apr 30, 2025
Could Gillian Anderson Reprise Her Role In A New X Files Series
Apr 30, 2025
