Cybercriminal's Office365 Heist: Millions In Losses Reported

Table of Contents
The Modus Operandi: How Cybercriminals Target Office365
Cybercriminals employ various methods to breach Office365 security, often combining several techniques for maximum impact. Understanding these tactics is crucial for effective defense.
Phishing and Spear Phishing Attacks
Phishing attacks remain a primary method for gaining unauthorized access to Office365 accounts. Criminals craft convincing emails that appear to originate from trusted sources, such as banks, colleagues, or even Microsoft itself. These emails often contain malicious links or attachments designed to:
- Install malware: This malware can range from keyloggers capturing login credentials to ransomware encrypting sensitive data, leading to significant data loss.
- Redirect to fake login pages: These mimic legitimate Office365 login screens, capturing user credentials entered by unsuspecting victims. This is a common tactic in Office365 compromise attempts.
- Deliver malicious macros: Embedded in seemingly harmless documents, these macros can execute harmful code once enabled.
Successful phishing campaigns against Office365 users are increasingly common. Statistics show that a significant percentage of successful breaches stem from successful phishing attempts, highlighting the effectiveness of this tactic and the need for robust email security.
Exploiting Weak Passwords and Credential Stuffing
Weak passwords, often reused across multiple platforms, are a significant vulnerability. Cybercriminals use readily available tools and techniques like credential stuffing to test these passwords against large databases of stolen credentials. This automated process can quickly compromise accounts with easily guessable or previously compromised passwords.
- Weak password examples: "password123," "123456," names of family members, etc.
- Credential stuffing: Automated tools try various password combinations against known usernames. This is often successful because many people reuse passwords across different platforms, making it easy for hackers to access accounts with a single compromised password.
The importance of strong, unique passwords and multi-factor authentication (MFA) cannot be overstated. MFA adds an extra layer of security, making it significantly harder for cybercriminals to gain access even if they obtain a password.
Compromised Third-Party Applications
Many businesses integrate third-party applications with their Office365 environment for enhanced functionality. However, vulnerabilities in these applications can create a backdoor for cybercriminals. A compromised third-party app might grant unauthorized access to Office365 data, resulting in a significant Office365 data breach.
- Insufficient vetting: Failing to thoroughly research and vet third-party apps before integration can lead to security risks.
- Outdated apps: Using outdated apps with known vulnerabilities increases the risk of exploitation.
Regular security audits and assessments are necessary to identify and address potential vulnerabilities in third-party applications connected to your Office365 environment.
The Devastating Consequences of an Office365 Breach
An Office365 breach can have far-reaching and devastating consequences, impacting an organization on multiple levels.
Financial Losses
Data breaches lead to significant financial losses, including:
- Ransomware payments: Cybercriminals often demand hefty ransoms for the release of encrypted data.
- Legal fees and regulatory fines: Organizations face potential lawsuits and fines for failing to comply with data protection regulations like GDPR and CCPA.
- Recovery costs: The cost of recovering data, restoring systems, and notifying affected individuals can be substantial.
Examples of large-scale Office365 breaches illustrate the millions of dollars in losses companies can suffer.
Reputational Damage
Data breaches severely damage an organization's reputation and erode customer trust. This can result in:
- Loss of customers: Customers may switch to competitors after a breach, fearing the security of their data.
- Loss of business opportunities: Damage to reputation can make it difficult to secure new contracts or partnerships.
The long-term impact on a company's image and brand can be significant, impacting its ability to operate effectively.
Legal and Regulatory Compliance Issues
Data breaches trigger significant legal and regulatory issues. Non-compliance with regulations such as GDPR (General Data Protection Regulation) and CCPA (California Consumer Privacy Act) can result in:
- Heavy fines: Organizations can face substantial fines for failing to protect customer data.
- Lawsuits: Affected individuals may file lawsuits seeking compensation for damages caused by the data breach.
Protecting Your Organization from Office365 Heists
Protecting your organization from Office365 heists requires a multi-layered approach incorporating several essential strategies.
Implementing Multi-Factor Authentication (MFA)
MFA significantly enhances Office365 security by requiring multiple forms of authentication to access accounts. Even if a password is compromised, MFA prevents unauthorized access.
- Methods: Common MFA methods include one-time codes sent via SMS, authentication apps (like Google Authenticator or Microsoft Authenticator), or security keys.
Implementing MFA is one of the most effective steps to prevent unauthorized access and minimize the risk of an Office365 compromise.
Regular Security Awareness Training
Educating employees about phishing scams, malware, and other cyber threats is crucial. Regular security awareness training should cover:
- Identifying phishing emails: Training employees to spot suspicious emails and links is critical.
- Password security: Enforce strong password policies and educate employees about password best practices.
- Safe internet practices: Educate employees on safe browsing habits and the risks of downloading files from untrusted sources.
Employing Advanced Threat Protection (ATP)
Microsoft's Advanced Threat Protection (ATP) provides advanced capabilities to detect and prevent sophisticated attacks targeting Office365. ATP features include:
- Anti-phishing and anti-malware protection: ATP proactively identifies and blocks malicious emails and attachments.
- Threat intelligence: Leveraging real-time threat intelligence to detect and respond to emerging threats.
- Investigation and response tools: Providing tools to investigate security incidents and take appropriate action.
Investing in ATP significantly enhances your overall Office365 security posture.
Regular Security Audits and Penetration Testing
Regular security audits and penetration testing identify vulnerabilities in your Office365 environment before cybercriminals can exploit them. These assessments:
- Identify weaknesses: Regular audits uncover potential security gaps in your systems and processes.
- Simulate attacks: Penetration testing simulates real-world attacks to test your security defenses.
- Improve security posture: The insights gained from these assessments allow you to strengthen your security posture and mitigate risks proactively.
Conclusion
The rise in Office365 heists underscores the critical need for proactive and robust security measures. Millions are being lost due to sophisticated cyberattacks that exploit vulnerabilities in user behavior and system configurations. By implementing multi-factor authentication, providing comprehensive security awareness training, leveraging advanced threat protection tools, and conducting regular security audits, organizations can significantly reduce their risk of falling victim to these devastating attacks. Don't wait until it's too late – secure your Office365 environment today and protect your valuable data from the ever-evolving threats of cybercriminals. Take control of your Office365 security now and prevent becoming the next victim of an Office365 data breach.

Featured Posts
-
 Ice Parent Nyse Exceeds Q1 Profit Expectations Due To Strong Trading Volume
May 14, 2025
Ice Parent Nyse Exceeds Q1 Profit Expectations Due To Strong Trading Volume
May 14, 2025 -
 Heartwarming Video Scotty Mc Creerys Son Pays Tribute To George Strait
May 14, 2025
Heartwarming Video Scotty Mc Creerys Son Pays Tribute To George Strait
May 14, 2025 -
 Short Lived Coaching Partnership For Raducanu
May 14, 2025
Short Lived Coaching Partnership For Raducanu
May 14, 2025 -
 Latest Company News Highlights Monday 1 Am Et
May 14, 2025
Latest Company News Highlights Monday 1 Am Et
May 14, 2025 -
 The Next King Of Country Parker Mc Collum Eyes George Straits Crown
May 14, 2025
The Next King Of Country Parker Mc Collum Eyes George Straits Crown
May 14, 2025
Latest Posts
-
 Waldbrandpraevention Moderne Technologien Fuer Den Nationalpark Schutz
May 14, 2025
Waldbrandpraevention Moderne Technologien Fuer Den Nationalpark Schutz
May 14, 2025 -
 Moderne Technik Zur Waldbrandfrueherkennung Ein Ueberblick Fuer Sachsen
May 14, 2025
Moderne Technik Zur Waldbrandfrueherkennung Ein Ueberblick Fuer Sachsen
May 14, 2025 -
 Hohburkersdorf Lagebericht Entwarnung In Der Saechsischen Schweiz Osterzgebirge
May 14, 2025
Hohburkersdorf Lagebericht Entwarnung In Der Saechsischen Schweiz Osterzgebirge
May 14, 2025 -
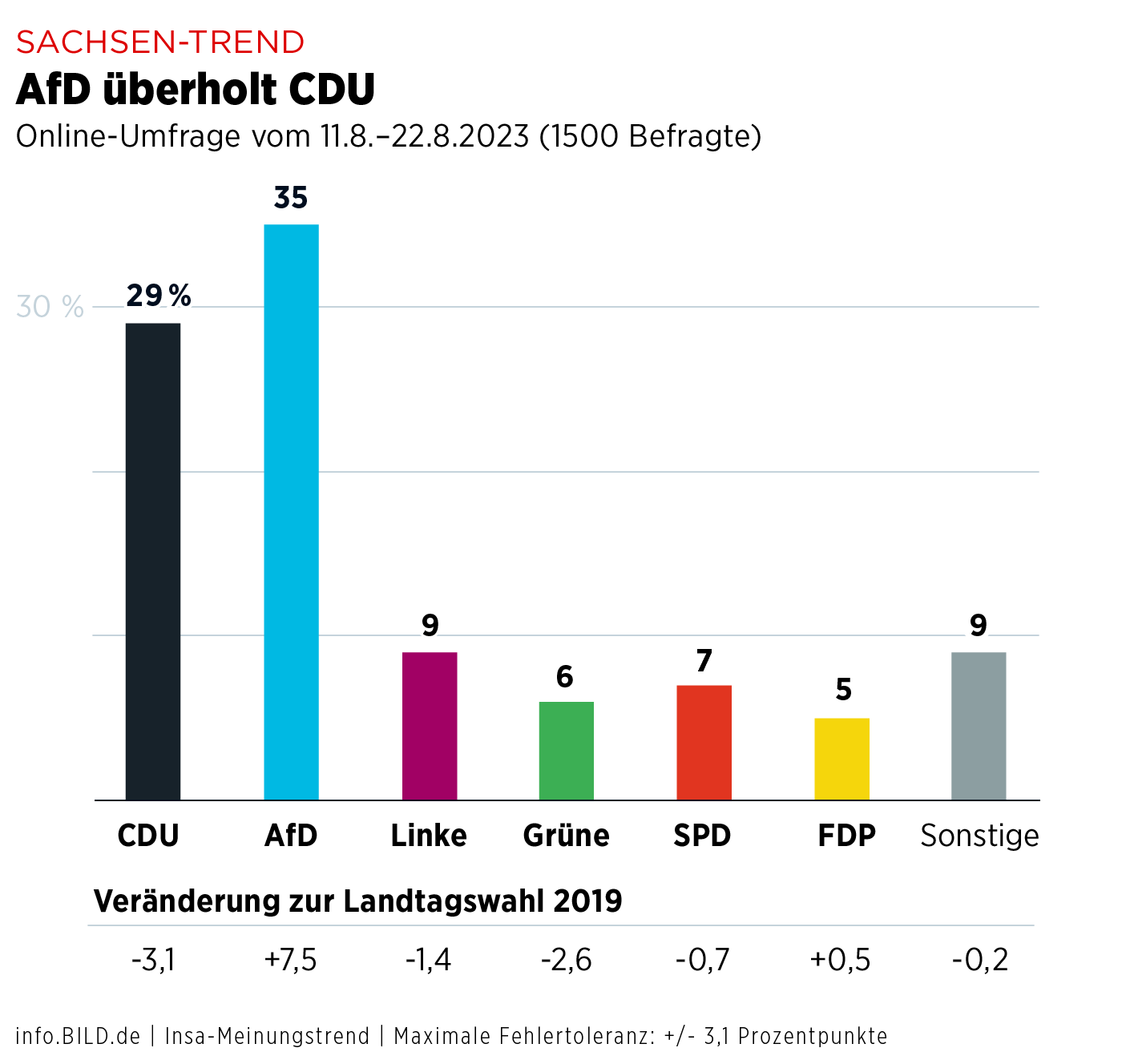 Kommunalwahl Dresden Deutliche Ablehnung Von Cdu Und Spd 80 Waehlerstimmen Anders Verteilt
May 14, 2025
Kommunalwahl Dresden Deutliche Ablehnung Von Cdu Und Spd 80 Waehlerstimmen Anders Verteilt
May 14, 2025 -
 Bad Gottleuba Berggiesshuebel Brandopfer Nach Wohnungsbrand Gefunden
May 14, 2025
Bad Gottleuba Berggiesshuebel Brandopfer Nach Wohnungsbrand Gefunden
May 14, 2025
