Cybercriminal's Millions: The Office365 Executive Email Compromise
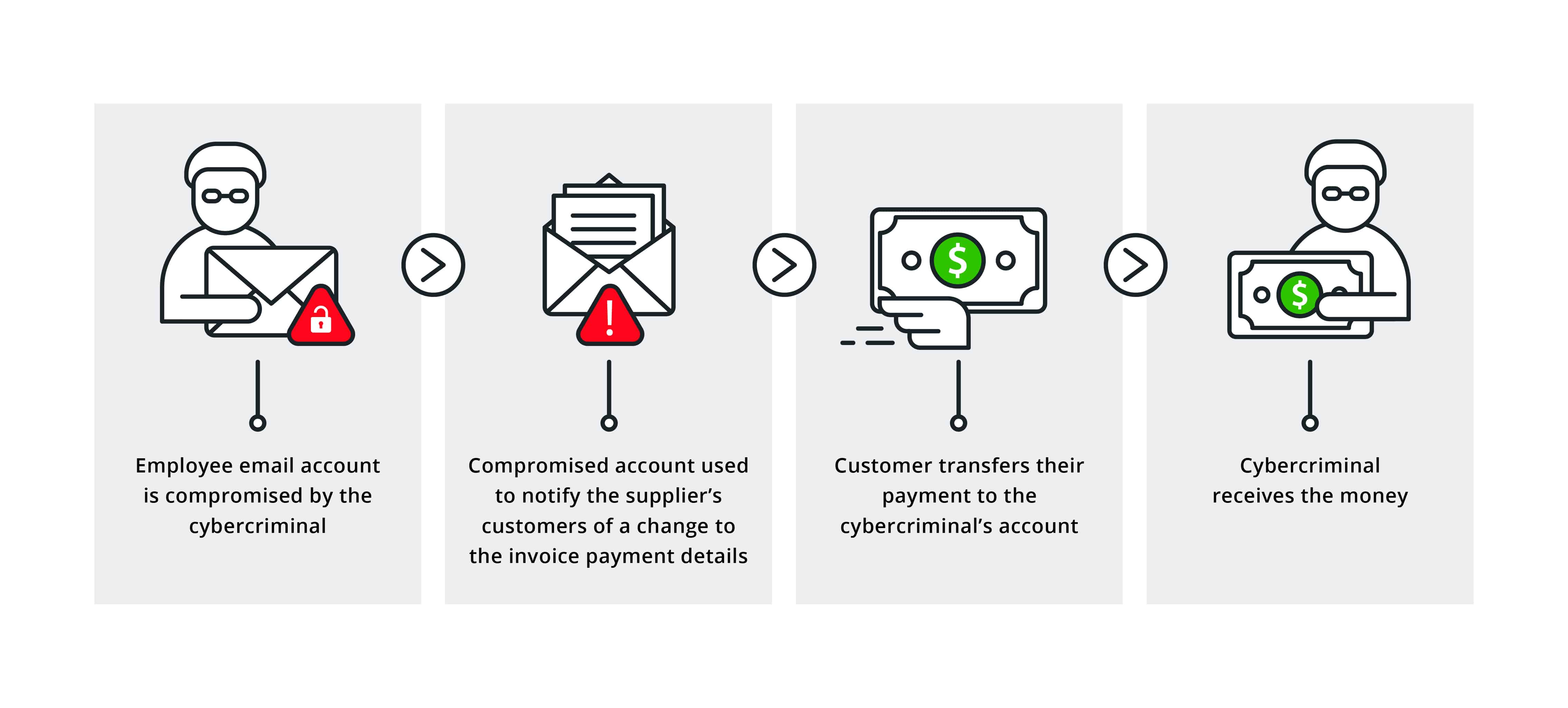
Table of Contents
Understanding Office365 Executive Email Compromise (EEC)
How EEC Attacks Work
Office365 EEC attacks are sophisticated phishing campaigns designed to deceive executives into authorizing fraudulent transactions. Cybercriminals meticulously research their targets, gathering information to craft highly personalized phishing emails and messages that appear legitimate. These attacks often involve a combination of techniques:
- Phishing emails mimicking legitimate communications: These emails may appear to be from a trusted colleague, business partner, or even a senior executive within the organization. They frequently contain urgent requests demanding immediate action.
- Compromised accounts through credential theft: Attackers might gain access to an executive's account through credential stuffing (using stolen credentials from other data breaches) or by exploiting vulnerabilities in less secure systems.
- Exploiting vulnerabilities in Office 365 integrations: Attackers might target weaknesses in third-party applications or integrations connected to Office 365.
- Using social engineering to manipulate executives: This involves manipulating the executive's psychology to pressure them into acting quickly and without proper verification. They might exploit the executive's authority and trust to bypass normal security protocols.
The attack typically follows these steps: initial phishing email, gaining access to the account, observing internal communication, identifying financial processes, and finally, initiating fraudulent transactions, often wire transfers. The infamous 2016 attack on the Democratic National Committee, leveraging spear phishing against high-ranking officials, serves as a stark example of the devastating consequences. The financial losses can run into millions.
The High Cost of EEC for Businesses
The financial impact of an Office365 EEC attack extends far beyond the immediate monetary loss. The consequences can include:
- Direct financial losses from fraudulent wire transfers: This is the most immediate and often most significant cost.
- Costs associated with incident response and remediation: Investigating the breach, containing the damage, and restoring systems can be incredibly expensive. Hiring cybersecurity experts and legal counsel adds to the burden.
- Loss of sensitive intellectual property: If the attackers gain access to company data, the loss of sensitive information can have long-term repercussions.
- Damage to brand reputation and customer trust: A publicized EEC attack can severely damage a company's reputation, leading to a loss of customers and investors.
The overall cost can be crippling, impacting shareholder confidence and potentially leading to significant legal ramifications. Consider the potential fines and lawsuits resulting from regulatory non-compliance.
Protecting Your Organization from Office365 EEC Attacks
Implementing Robust Security Measures
The best defense against Office365 EEC attacks is a multi-layered security approach. Critical measures include:
- Enforce multi-factor authentication (MFA) for all accounts: MFA adds an extra layer of security, making it significantly harder for attackers to access accounts even if they obtain passwords.
- Implement advanced threat protection (ATP) solutions: ATP solutions can detect and block malicious emails and attachments before they reach users' inboxes.
- Regularly update software and patches: Keeping software up-to-date patches vulnerabilities that attackers might exploit.
- Conduct employee security awareness training: Educating employees about the signs of phishing emails and other social engineering tactics is crucial. Regular training reinforces good security practices.
- Employ strong password policies and password management: Implementing strong password policies and using password managers can significantly reduce the risk of credential theft.
These measures significantly reduce the vulnerability of your organization to targeted attacks.
Recognizing and Responding to Suspicious Activity
Employee vigilance is paramount in preventing and responding to EEC attacks. Employees should be trained to identify red flags, including:
- Urgent requests for wire transfers or payments: Legitimate requests rarely demand immediate action without verification.
- Unusual email addresses or domains: Look for slight variations in familiar email addresses or unfamiliar domain names.
- Grammatical errors or suspicious links: Poor grammar or unusual links often indicate phishing attempts.
- Unusual attachment types: Be wary of unexpected attachments, especially executable files.
- Pressure to act quickly without verification: Legitimate requests rarely pressure recipients to act without proper checks and balances.
If an EEC attack is suspected, immediate action is critical. Isolate affected accounts, contact your IT department immediately, and follow your organization's incident response plan.
Conclusion
Office365 Executive Email Compromise attacks pose a significant threat to businesses of all sizes. The financial and reputational consequences can be devastating. By implementing robust security measures, including multi-factor authentication (MFA), advanced threat protection (ATP), and comprehensive employee training, organizations can significantly reduce their vulnerability. Don't become another statistic. Protect your business from costly Office365 Executive Email Compromise attacks by implementing robust security measures today!

Featured Posts
-
 Americas Best Beaches 2025 Dr Beachs Top 10
May 24, 2025
Americas Best Beaches 2025 Dr Beachs Top 10
May 24, 2025 -
 Pandemic Fraud Lab Owner Convicted For False Covid Test Results
May 24, 2025
Pandemic Fraud Lab Owner Convicted For False Covid Test Results
May 24, 2025 -
 Al Rokers Off The Record Comments Spark Today Show Controversy
May 24, 2025
Al Rokers Off The Record Comments Spark Today Show Controversy
May 24, 2025 -
 Reopening The Dreyfus Case A Parliamentary Push For Recognition
May 24, 2025
Reopening The Dreyfus Case A Parliamentary Push For Recognition
May 24, 2025 -
 Global Healthcare Transformation Insights From The Philips Future Health Index 2025 On Ai
May 24, 2025
Global Healthcare Transformation Insights From The Philips Future Health Index 2025 On Ai
May 24, 2025
Latest Posts
-
 Gideon Glick Et Jonathan Groff Retrouvailles Memorables Dans Etoile
May 24, 2025
Gideon Glick Et Jonathan Groff Retrouvailles Memorables Dans Etoile
May 24, 2025 -
 Etoile La Comedie Musicale Qui Reunit Gideon Glick Et Jonathan Groff
May 24, 2025
Etoile La Comedie Musicale Qui Reunit Gideon Glick Et Jonathan Groff
May 24, 2025 -
 Une Scene Hilarante De Spring Awakening La Reunion De Gideon Glick Et Jonathan Groff Grace A Etoile
May 24, 2025
Une Scene Hilarante De Spring Awakening La Reunion De Gideon Glick Et Jonathan Groff Grace A Etoile
May 24, 2025 -
 Jonathan Groffs Just In Time A Night Of Support From Lea Michele And Fellow Stars
May 24, 2025
Jonathan Groffs Just In Time A Night Of Support From Lea Michele And Fellow Stars
May 24, 2025 -
 Etoile Gideon Glick Et Jonathan Groff Reunis Dans Une Scene Hilarante De Spring Awakening
May 24, 2025
Etoile Gideon Glick Et Jonathan Groff Reunis Dans Une Scene Hilarante De Spring Awakening
May 24, 2025
