Cybercriminal Makes Millions From Compromised Executive Office365 Accounts
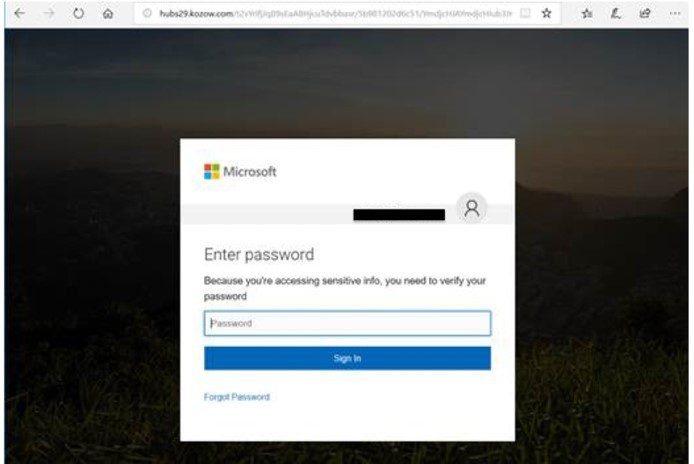
Table of Contents
The Modus Operandi: How the Cybercriminal Targeted Executive Office365 Accounts
This cybercriminal employed a multi-pronged approach to target executive Office365 accounts, focusing on exploiting human vulnerabilities and technical weaknesses.
Sophisticated Phishing Campaigns:
The cybercriminal launched highly targeted phishing campaigns designed to bypass sophisticated spam filters. These weren't generic phishing attempts; instead, they utilized:
- Highly personalized emails: Emails were tailored to the specific recipient, referencing internal projects, company events, or even personal details gleaned from social media.
- Social engineering techniques: The emails employed pressure tactics, creating a sense of urgency or fear to manipulate recipients into clicking malicious links or downloading infected attachments. This included impersonating trusted colleagues or superiors.
- Exploiting older Office365 versions: The attacks specifically targeted organizations running outdated versions of Office365, taking advantage of known vulnerabilities that had been patched in later releases.
- Deceptive email subject lines and content: Subject lines mimicked legitimate business communications, such as "Urgent Invoice," "Important Contract," or "Meeting Confirmation." Email content was crafted to appear authentic and convincing. For instance, one email purportedly contained a crucial financial document requiring immediate attention.
Exploiting Weak Passwords and Authentication:
A significant contributing factor to the success of these attacks was the prevalence of weak or reused passwords amongst executives. The lack of multi-factor authentication (MFA) further exacerbated the vulnerability. The cybercriminal employed:
- Password cracking techniques: Brute-force attacks and dictionary attacks were used to crack weak passwords. Reused passwords across multiple platforms made this task even easier.
- Credential stuffing: The cybercriminal likely used stolen credentials from other data breaches to attempt logins to the compromised Office365 accounts.
- The importance of strong password management policies: The lack of robust password policies, including password complexity requirements and regular password changes, allowed the cybercriminal easy access. This case underscores the crucial need for strong password management practices.
Post-Compromise Actions:
Once access was gained, the cybercriminal systematically exploited the compromised accounts to:
- Access sensitive financial data: This included bank account details, wire transfer information, and internal financial reports.
- Initiate wire transfers: Millions of dollars were illegally transferred to offshore accounts controlled by the cybercriminal.
- Manipulate financial records: The cybercriminal altered financial records to conceal the fraudulent transactions.
- Potential use for ransomware attacks: Although not confirmed in this specific case, compromised accounts could have been used to launch further attacks, such as ransomware deployments, against the organization.
- Data exfiltration: Sensitive internal communications and intellectual property were potentially exfiltrated, causing further damage.
The Financial Impact: Millions Lost Through Office365 Account Breaches
The financial impact of these Office365 account breaches was substantial, extending far beyond the direct monetary losses.
Scale of the Financial Loss:
The victimized organizations suffered losses totaling millions of dollars. The exact figures are not publicly available due to confidentiality concerns, but the scale of the financial damage highlights the significant risk posed by these attacks.
Direct Financial Losses:
The direct losses included:
- Wire transfers: Millions were siphoned off through fraudulent wire transfers.
- Fraudulent payments: Fake invoices and payments were processed, draining company resources.
- Extortion demands: In some instances, the cybercriminal may have demanded ransom payments to prevent further data leaks or disruption.
Indirect Costs:
Beyond the direct financial losses, significant indirect costs were incurred, including:
- Legal fees: The organizations had to engage legal counsel to investigate the breaches and mitigate potential legal liabilities.
- Public relations damage control: The reputational damage required extensive PR efforts to restore public trust.
- Loss of productivity: The disruption caused by the breaches led to significant loss of productivity while investigations and remediation efforts were underway.
Long-Term Impact:
The long-term consequences include:
- Damaged reputation: The breaches severely damaged the reputation of the affected organizations, impacting investor confidence and business relationships.
- Loss of investor confidence: The news of data breaches can significantly impact investor confidence and lead to a decline in share prices.
Protecting Your Organization: Best Practices for Office365 Security
Protecting your organization from similar attacks requires a multi-layered approach focused on both technical and human elements.
Implementing Multi-Factor Authentication (MFA):
MFA is crucial in preventing account takeovers, even if passwords are compromised. Implementing MFA adds an extra layer of security, requiring users to provide multiple forms of authentication, such as a password and a one-time code from their mobile device.
Employee Security Awareness Training:
Regular security awareness training is essential to educate employees about phishing scams and other social engineering tactics. This includes training on:
- Recognizing phishing emails: Teaching employees how to identify the red flags of phishing emails.
- Safe browsing practices: Educating employees on how to avoid clicking on suspicious links.
- Password hygiene: Reinforcing the importance of strong, unique passwords and password management best practices.
Regular Security Audits and Penetration Testing:
Regular security audits and penetration testing help identify vulnerabilities in your organization’s security infrastructure. These assessments can reveal weaknesses that cybercriminals could exploit.
Robust Password Management Policies:
Enforce strong password policies, including:
- Password complexity requirements: Mandate the use of strong passwords that meet certain complexity criteria.
- Regular password changes: Require regular password changes to minimize the impact of compromised passwords.
- Password managers: Encourage the use of secure password managers to store and manage passwords securely.
Utilizing Advanced Threat Protection:
Leverage Office365's built-in advanced threat protection features to detect and block malicious emails and attachments.
Regular Software Updates and Patching:
Keep all software, including Office365, up-to-date with the latest security patches to mitigate known vulnerabilities.
Conclusion:
This case study of a cybercriminal profiting from compromised executive Office365 accounts serves as a stark warning. The financial and reputational damage from such breaches can be catastrophic. The vulnerabilities exploited – weak passwords, lack of MFA, and susceptibility to phishing – highlight the critical need for proactive security measures. Don't become another victim of Office365 account compromise. Invest in robust cybersecurity practices, including MFA, comprehensive employee training, regular security audits, and advanced threat protection. Protect your organization and its valuable data by implementing strong Office365 security measures today.

Featured Posts
-
 Which Cruise Lines Are Owned By Carnival A Comprehensive Guide
May 01, 2025
Which Cruise Lines Are Owned By Carnival A Comprehensive Guide
May 01, 2025 -
 Investing In Norwegian Cruise Line Nclh Examining Hedge Fund Sentiment
May 01, 2025
Investing In Norwegian Cruise Line Nclh Examining Hedge Fund Sentiment
May 01, 2025 -
 Alqdyt Dd Ryys Shbab Bn Jryr Tfasyl Alhkm Walmeaqbt
May 01, 2025
Alqdyt Dd Ryys Shbab Bn Jryr Tfasyl Alhkm Walmeaqbt
May 01, 2025 -
 Filmmakers Sue Michael Sheen And Channel 4 For Copyright Infringement
May 01, 2025
Filmmakers Sue Michael Sheen And Channel 4 For Copyright Infringement
May 01, 2025 -
 Gia Tieu Hom Nay Tin Tuc Thi Truong Tieu Moi Nhat
May 01, 2025
Gia Tieu Hom Nay Tin Tuc Thi Truong Tieu Moi Nhat
May 01, 2025
