Crook's Office365 Hacking Spree: Millions In Losses For Executives

Table of Contents
Sophisticated Tactics Employed in the Office365 Hacking Spree
The Crook's Office365 Hacking Spree demonstrated a disturbingly high level of sophistication in its tactics. Attackers leveraged a combination of techniques to breach security and gain access to sensitive information.
Phishing and Spear Phishing Attacks
Phishing and spear phishing emails remain the most common entry point for Office365 breaches. These attacks often appear incredibly convincing, mimicking legitimate communications from trusted sources.
- Example 1: Attackers might impersonate a CEO, sending an urgent email to a financial executive requesting an immediate wire transfer.
- Example 2: A spear phishing campaign could target a specific company, using insider information obtained through open-source intelligence to craft highly personalized and believable emails.
- Attackers exploit vulnerabilities in email security protocols, often bypassing basic spam filters through the use of sophisticated techniques like email spoofing and bypassing SPF, DKIM, and DMARC authentication.
- Malicious attachments (e.g., infected documents or executables) and links leading to compromised websites are frequently used to deliver malware or steal credentials.
Credential Stuffing and Brute-Force Attacks
Even with strong email security, weak passwords remain a significant vulnerability. Attackers often employ credential stuffing, using lists of stolen usernames and passwords from other breaches to attempt access to Office365 accounts. Brute-force attacks systematically try various password combinations until they find the correct one.
- Strong, unique passwords are essential, incorporating uppercase and lowercase letters, numbers, and symbols.
- Password managers can help generate and securely store strong, unique passwords for each account.
- Multi-factor authentication (MFA) adds an extra layer of security, requiring users to provide a second form of authentication (e.g., a code sent to their phone) in addition to their password.
Exploiting Vulnerable Third-Party Apps
Many businesses integrate third-party applications with their Office365 environment. Hackers can exploit vulnerabilities in these applications to gain unauthorized access.
- Thoroughly vet all third-party applications before integrating them with Office365.
- Regular security audits of connected apps are crucial to identify and address potential vulnerabilities.
- Ensure all third-party apps undergo regular security updates and patches.
The Devastating Financial and Reputational Consequences
The impact of an Office365 security breach extends far beyond the initial compromise. The consequences can be financially crippling and severely damage a company's reputation.
Direct Financial Losses
The financial fallout from an Office365 hacking incident can be substantial.
- Ransomware attacks can encrypt crucial data, demanding significant payments for its release.
- Data recovery and forensic investigation costs can run into tens of thousands of dollars.
- Legal fees associated with data breach notifications and potential lawsuits can be substantial.
- Loss of intellectual property (IP) theft can lead to irreversible financial damage and competitive disadvantage.
Reputational Damage and Loss of Customer Trust
The reputational harm caused by an Office365 security breach can be long-lasting.
- Damage to brand image and loss of customer trust can lead to decreased sales and revenue.
- Investor confidence can plummet, affecting stock prices and access to capital.
- Legal ramifications, including fines and penalties for non-compliance with data protection regulations (like GDPR), can further exacerbate financial losses.
Protecting Your Organization from Office365 Hacks
Proactive steps are crucial in mitigating the risk of Office365 hacking. A multi-layered approach is essential.
Implementing Robust Security Measures
Investing in robust security measures is the first line of defense against Office365 attacks.
- Multi-factor authentication (MFA): Mandate MFA for all users to significantly reduce the risk of unauthorized access.
- Security awareness training: Regularly train employees to recognize and avoid phishing scams and other social engineering tactics.
- Advanced threat protection tools: Utilize advanced security solutions to detect and prevent malicious emails, attachments, and links.
Regular Security Audits and Vulnerability Assessments
Proactive security checks are essential for identifying and addressing potential weaknesses before they can be exploited.
- Penetration testing: Simulate real-world attacks to identify vulnerabilities in your Office365 environment.
- Regular software updates: Ensure all software and applications are updated with the latest security patches.
Developing a Comprehensive Incident Response Plan
Having a well-defined incident response plan is crucial for minimizing the impact of a breach.
- Establish clear procedures for identifying, containing, and remediating a security incident.
- Develop a communication plan to inform affected stakeholders and regulatory bodies.
Conclusion: Strengthening Office365 Security to Avoid Becoming a Victim
The Crook's Office365 Hacking Spree highlights the devastating financial and reputational consequences of neglecting Office365 security. Proactive measures, including strong passwords, MFA, robust security awareness training, and regular security audits, are essential to prevent becoming a victim. Don't let your organization become the next victim. Invest in robust Office365 security today! For further information on enhancing your Office365 security, explore resources like Microsoft's Security documentation and reputable cybersecurity firms specializing in Office 365 security.

Featured Posts
-
 Police Respond To Cherry Hill Shooting One Man Injured
May 29, 2025
Police Respond To Cherry Hill Shooting One Man Injured
May 29, 2025 -
 Seattle Police Investigating First Hill Homicide Public Assistance Needed
May 29, 2025
Seattle Police Investigating First Hill Homicide Public Assistance Needed
May 29, 2025 -
 Spring Valley Dominates Spring Mills 88 36 Victory
May 29, 2025
Spring Valley Dominates Spring Mills 88 36 Victory
May 29, 2025 -
 Experience The Stranger Things Universe Comics To Keep You Engaged Until Season 5
May 29, 2025
Experience The Stranger Things Universe Comics To Keep You Engaged Until Season 5
May 29, 2025 -
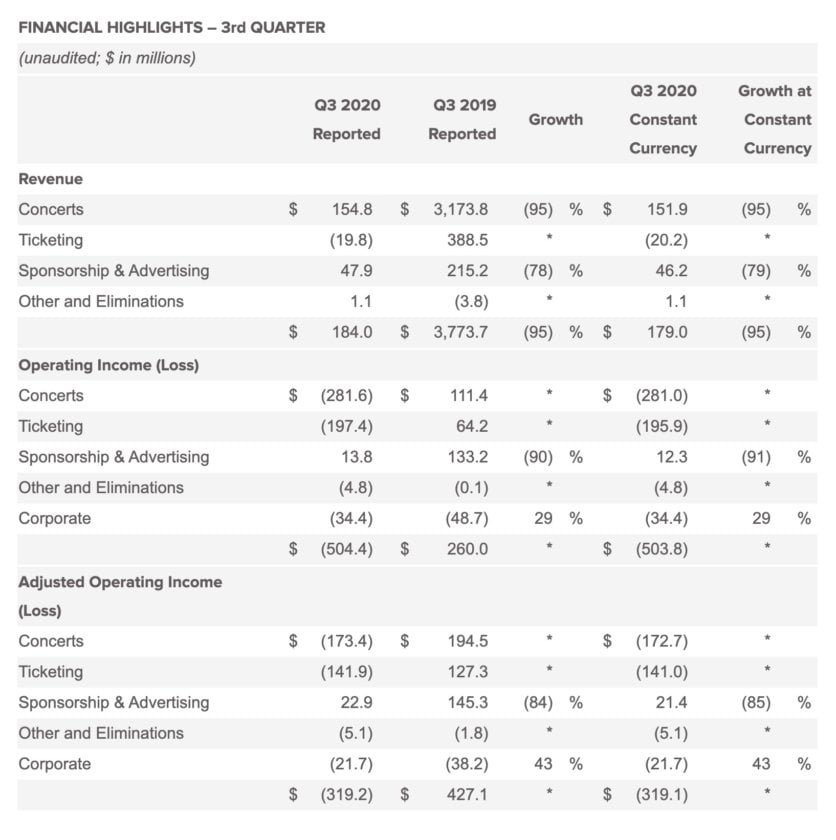 Is Live Nation Stifling Competition In The Live Music Market A Wsj Investigation
May 29, 2025
Is Live Nation Stifling Competition In The Live Music Market A Wsj Investigation
May 29, 2025
