Crook Accused Of Millions In Office365 Executive Email Account Breaches

Table of Contents
The Modus Operandi: How the Office365 Executive Email Account Breaches Were Executed
This sophisticated attack likely involved a multi-stage process leveraging several common cybercriminal tactics. Understanding these methods is crucial for implementing effective preventative measures.
-
Spear-phishing and Social Engineering: The crook likely employed highly targeted spear-phishing emails designed to appear legitimate and entice executives to click malicious links or download infected attachments. These emails may have mimicked trusted sources, like internal communications or legitimate business partners, to increase their credibility and bypass email filters. Sophisticated social engineering techniques might have been used to gather information about the target executives, personalizing the phishing attempts for maximum impact.
-
Malware Deployment: Successful phishing attacks often lead to malware deployment. This could range from keyloggers silently recording keystrokes to steal login credentials, to more advanced malware capable of establishing persistent access to the compromised accounts and systems. This persistent access allows the attacker to maintain control over the accounts even after the initial compromise.
-
Exploiting Office365 Vulnerabilities and User Practices: The attacker might have exploited vulnerabilities in Office365 settings or weak security practices within the targeted organizations. This could include weak passwords, a lack of multi-factor authentication (MFA), or outdated software. The attacker might have also leveraged vulnerabilities in third-party applications integrated with Office365.
-
Credential Stuffing and Automated Attacks: In addition to targeted attacks, credential stuffing – using stolen credentials from other breaches to attempt logins – may have been used to identify potentially vulnerable accounts. Automated tools can accelerate this process, testing numerous username/password combinations.
-
Lack of Robust Multi-Factor Authentication (MFA): The absence of strong multi-factor authentication (MFA), or a weak implementation of MFA, is a significant factor that could have enabled the success of this attack. MFA adds a critical layer of security, making it significantly harder for attackers to gain access even if they obtain usernames and passwords.
The Financial Impact: Millions Lost Through Compromised Office365 Accounts
The financial consequences of this Office365 executive email account breach are substantial, highlighting the high cost of cybercrime. While precise figures may not be publicly available, the reported millions lost underscore the devastating impact.
-
Business Email Compromise (BEC) and Wire Fraud: The compromised accounts were likely used to execute Business Email Compromise (BEC) schemes, including wire fraud. The crook probably manipulated email communication to trick the victim's financial department into transferring large sums of money to fraudulent accounts.
-
Invoice Fraud and Account Takeover: Another likely tactic involves invoice fraud, where the crook altered invoices to redirect payments to their own accounts. Account takeover allowed the criminal to access and control financial systems, enabling direct manipulation of funds.
-
Long-Term Reputational Damage and Legal Consequences: Beyond the direct financial losses, these breaches cause significant reputational damage. Victimized companies face potential legal repercussions, regulatory fines, and loss of client trust.
-
Overall Cost Estimation: The total cost includes not only the financial losses but also the expenses associated with forensic investigations, legal fees, remediation efforts, and the long-term impact on the organization's reputation and business operations.
Strengthening Office365 Security: Prevention and Mitigation Strategies
Preventing similar Office365 breaches requires a multi-faceted approach focusing on technical security, user training, and proactive monitoring.
-
Implement Strong Passwords and Multi-Factor Authentication (MFA): Enforce strong, unique passwords and mandatory multi-factor authentication (MFA) for all users, especially executives. Consider using a strong password manager to assist users with securely managing and remembering their passwords.
-
Configure Office365 Security Settings: Utilize Office365's built-in security features, such as advanced threat protection, data loss prevention (DLP), and email authentication protocols like SPF, DKIM, and DMARC. Regularly review and update these settings based on best practices and emerging threats.
-
Employee Cybersecurity Awareness Training: Invest in comprehensive cybersecurity awareness training programs to educate employees about phishing attacks, social engineering tactics, and safe email practices. Regular simulations and phishing campaigns can significantly improve user vigilance.
-
Leverage Email Security Solutions and Data Loss Prevention (DLP) Tools: Implement advanced email security solutions that can detect and block malicious emails, attachments, and links. DLP tools can monitor and prevent sensitive data from leaving the organization’s network.
-
Regular Security Audits and Vulnerability Assessments: Conduct regular security audits and vulnerability assessments to identify and address potential weaknesses in your Office365 environment and overall IT infrastructure.
The Role of Human Error in Office365 Breaches
Human error is a significant contributing factor in many Office365 breaches. Even the most sophisticated technical security measures can be bypassed by a single click on a malicious link.
-
Social Engineering Bypasses Technical Security: Social engineering techniques exploit human psychology to trick users into compromising security protocols. These techniques often bypass technical security measures.
-
Importance of Comprehensive Employee Training: Comprehensive employee training and awareness programs are critical to mitigating the risk of human error. Training should focus on identifying and reporting phishing attempts, practicing safe email habits, and understanding the importance of security protocols.
-
Reinforcing Safe Email Practices: Regular reminders and reinforcement of safe email practices, such as verifying sender identities and avoiding suspicious links or attachments, are essential in building a security-conscious culture.
Conclusion
The case of the crook accused of millions in Office365 executive email account breaches serves as a stark reminder of the ever-evolving threats in the digital landscape. The sophisticated techniques employed underscore the need for robust security measures and vigilant employee training. The financial and reputational damage caused by these types of attacks can be devastating. Don't become another victim of Office365 executive email account breaches. Take proactive steps to strengthen your organization's cybersecurity posture today. Implement multi-factor authentication, conduct regular security assessments, and invest in comprehensive employee training. Secure your Office365 environment and protect your business from devastating financial and reputational loss. Prioritize your Office365 security to safeguard your business against this growing threat.

Featured Posts
-
 Dijital Veri Tabani Isguecue Piyasasi Rehberi Carsamba Ledra Pal Da
May 15, 2025
Dijital Veri Tabani Isguecue Piyasasi Rehberi Carsamba Ledra Pal Da
May 15, 2025 -
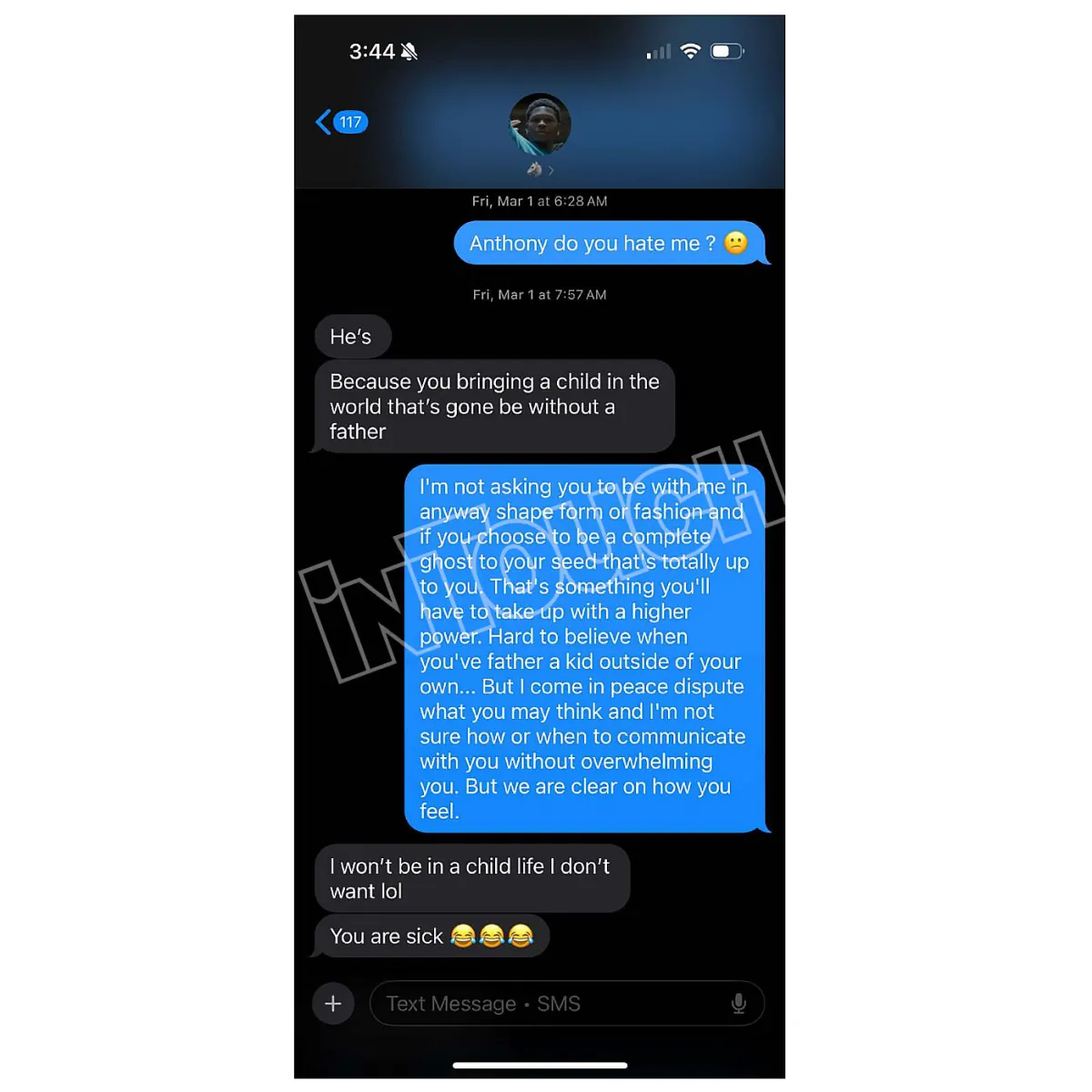 The Latest On Anthony Edwards And His Baby Mama Drama A Twitter Analysis
May 15, 2025
The Latest On Anthony Edwards And His Baby Mama Drama A Twitter Analysis
May 15, 2025 -
 Mls Injury Roundup Latest On Martinez And Whites Availability
May 15, 2025
Mls Injury Roundup Latest On Martinez And Whites Availability
May 15, 2025 -
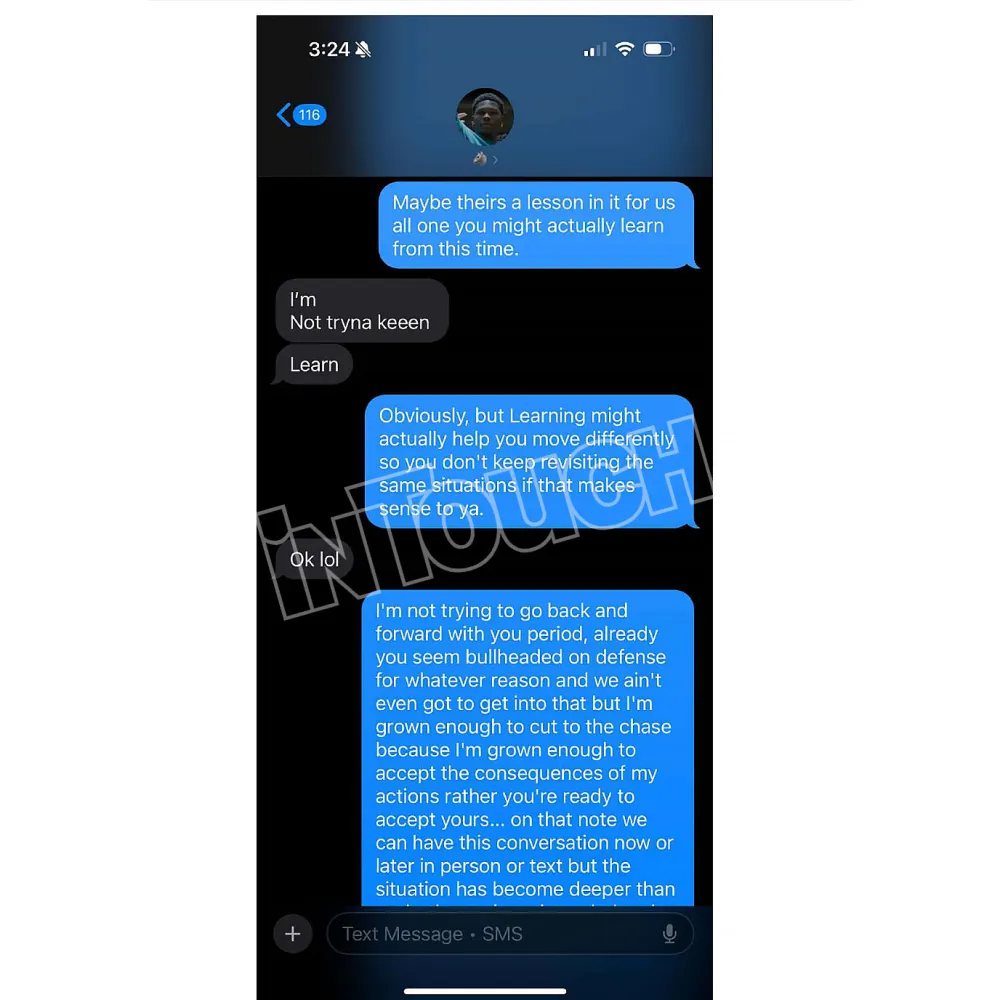 Co Parenting Success Ayesha Howard And Anthony Edwards Unique Family Dynamic
May 15, 2025
Co Parenting Success Ayesha Howard And Anthony Edwards Unique Family Dynamic
May 15, 2025 -
 Court Awards Ayesha Howard Custody After Anthony Edwards Paternity Dispute
May 15, 2025
Court Awards Ayesha Howard Custody After Anthony Edwards Paternity Dispute
May 15, 2025
Latest Posts
-
 Watch The Full Joe And Jill Biden Interview On The View
May 15, 2025
Watch The Full Joe And Jill Biden Interview On The View
May 15, 2025 -
 Analyzing Jd Vances Response To Bidens Ukraine Policy Critique
May 15, 2025
Analyzing Jd Vances Response To Bidens Ukraine Policy Critique
May 15, 2025 -
 Joe And Jill Bidens The View Interview Watch Now
May 15, 2025
Joe And Jill Bidens The View Interview Watch Now
May 15, 2025 -
 Miss Joe And Jill Biden On The View Full Interview
May 15, 2025
Miss Joe And Jill Biden On The View Full Interview
May 15, 2025 -
 Bidens Ukraine Remarks Jd Vances Effective Counter Argument
May 15, 2025
Bidens Ukraine Remarks Jd Vances Effective Counter Argument
May 15, 2025
