Corporate Email Hack: Millions Stolen Via Compromised Office365 Accounts

Table of Contents
The Methods Behind Office365 Corporate Email Hacks
Cybercriminals employ a range of cunning techniques to gain unauthorized access to Office365 accounts, leading to significant financial loss and data breaches. Understanding these methods is the first step towards effective prevention.
Phishing and Social Engineering
Phishing attacks remain a primary vector for Office365 account compromises. These attacks often involve deceptively crafted emails designed to trick employees into revealing their login credentials or downloading malicious software. Spear phishing, a more targeted approach, personalizes these emails to increase their effectiveness.
- How they work: Phishing emails might mimic legitimate communications from trusted sources, urging recipients to click links leading to fake login pages or attachments containing malware.
- Examples: Emails claiming to be from internal IT, requesting password resets, or notifying users of suspicious account activity.
- Employee Training: Regular security awareness training is crucial to equip employees with the skills to identify and avoid phishing attempts. This should include simulated phishing exercises and clear guidelines on safe email practices. Keywords: phishing attacks, spear phishing, social engineering, email security training.
Credential Stuffing and Brute-Force Attacks
Hackers frequently leverage stolen credentials from other platforms to attempt access to Office365 accounts using a technique known as credential stuffing. This involves testing combinations of usernames and passwords obtained from data breaches on other websites. Alternatively, brute-force attacks use automated tools to try various password combinations until they find a match.
- Importance of Strong Passwords: Employ strong, unique passwords for each online account. Avoid reusing passwords across different platforms.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security, requiring a second form of verification (e.g., a code sent to your phone) in addition to your password.
- Password Managers: Utilize password managers to generate and securely store strong, unique passwords for all your accounts. Keywords: credential stuffing, brute-force attack, password security, multi-factor authentication (MFA), password manager.
Exploiting Software Vulnerabilities
Outdated software and unpatched vulnerabilities in Office365 or related applications create significant entry points for hackers. These vulnerabilities can be exploited to gain unauthorized access, install malware, or steal sensitive data.
- Regular Software Updates: Ensure that all software, including Office365 and related applications, is regularly updated with the latest security patches.
- Vulnerability Scanning and Penetration Testing: Regularly conduct vulnerability scans and penetration testing to identify and address potential security weaknesses proactively. Keywords: software vulnerabilities, security patches, vulnerability scanning, penetration testing.
The Devastating Consequences of a Corporate Email Hack
The repercussions of a successful Office365 corporate email hack can be far-reaching and severely impact a business's bottom line and reputation.
Financial Losses
The financial impact of a data breach can be substantial. Costs include:
- Direct Monetary Theft: Hackers might directly steal funds through fraudulent transactions.
- Legal Fees: Responding to data breaches often involves significant legal expenses.
- Regulatory Fines: Non-compliance with data privacy regulations (like GDPR) can result in hefty fines.
- Reputational Damage: A data breach can severely damage a company's reputation, leading to lost customers and business opportunities. Keywords: financial impact, data breach costs, regulatory fines, reputational damage.
Data Breaches and Intellectual Property Theft
Compromised Office365 accounts can expose sensitive data, including:
- Customer Information: Names, addresses, credit card details, and other personally identifiable information.
- Intellectual Property: Trade secrets, patents, and other valuable intellectual property.
- GDPR and Data Privacy Regulations: Failure to protect sensitive data can lead to severe penalties under GDPR and other data privacy regulations. Keywords: data breach, intellectual property theft, GDPR, data privacy.
Operational Disruption and Loss of Productivity
A corporate email hack can severely disrupt business operations:
- Loss of Productivity: Employees might be unable to access email or other essential applications.
- Damage to Client Relationships: Compromised communication can damage trust and relationships with clients.
- Business Continuity and Disaster Recovery: Robust business continuity and disaster recovery plans are crucial to minimize disruption in the event of a breach. Keywords: business disruption, loss of productivity, business continuity, disaster recovery.
Protecting Your Office365 Account from Corporate Email Hacks
Proactive security measures are essential to safeguard your Office365 accounts and prevent corporate email hacks.
Implementing Strong Security Measures
- Multi-Factor Authentication (MFA): Enable MFA for all Office365 accounts.
- Strong Passwords and Password Management: Use strong, unique passwords and a password manager.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities.
- Employee Training: Provide ongoing security awareness training to employees. Keywords: Office365 security, cybersecurity best practices, security audit, security awareness training.
Utilizing Advanced Threat Protection (ATP)
Microsoft's Advanced Threat Protection (ATP) and similar services provide robust protection against advanced threats:
- Anti-phishing: Detects and blocks phishing emails.
- Anti-malware: Protects against malware and other malicious software.
- URL Filtering: Blocks access to malicious websites. Keywords: Microsoft ATP, advanced threat protection, anti-phishing, anti-malware, URL filtering.
Conclusion: Safeguarding Your Business from Office365 Corporate Email Hacks
The threat of Office365 corporate email hacks is real and the consequences can be devastating. Financial losses, data breaches, and operational disruptions are just some of the potential outcomes. Proactive security measures, including implementing multi-factor authentication, strong passwords, regular security audits, employee training, and utilizing advanced threat protection services, are crucial for protecting your business from these attacks. Don't wait until it's too late; take decisive action today to safeguard your Office365 accounts and mitigate the risk of significant financial loss. Consider consulting with a cybersecurity professional for a comprehensive assessment and tailored security plan to further enhance your protection against Office365 corporate email hacks.

Featured Posts
-
 Frances Rugby Dominance A Detailed Look At Duponts Performance
May 02, 2025
Frances Rugby Dominance A Detailed Look At Duponts Performance
May 02, 2025 -
 Fortnite Update 34 30 Server Downtime Patch Notes And Whats New
May 02, 2025
Fortnite Update 34 30 Server Downtime Patch Notes And Whats New
May 02, 2025 -
 Loyle Carner To Play Dublins 3 Arena
May 02, 2025
Loyle Carner To Play Dublins 3 Arena
May 02, 2025 -
 Priscilla Pointer Dead At 100 Remembering The Carrie Actress And Her Daughter
May 02, 2025
Priscilla Pointer Dead At 100 Remembering The Carrie Actress And Her Daughter
May 02, 2025 -
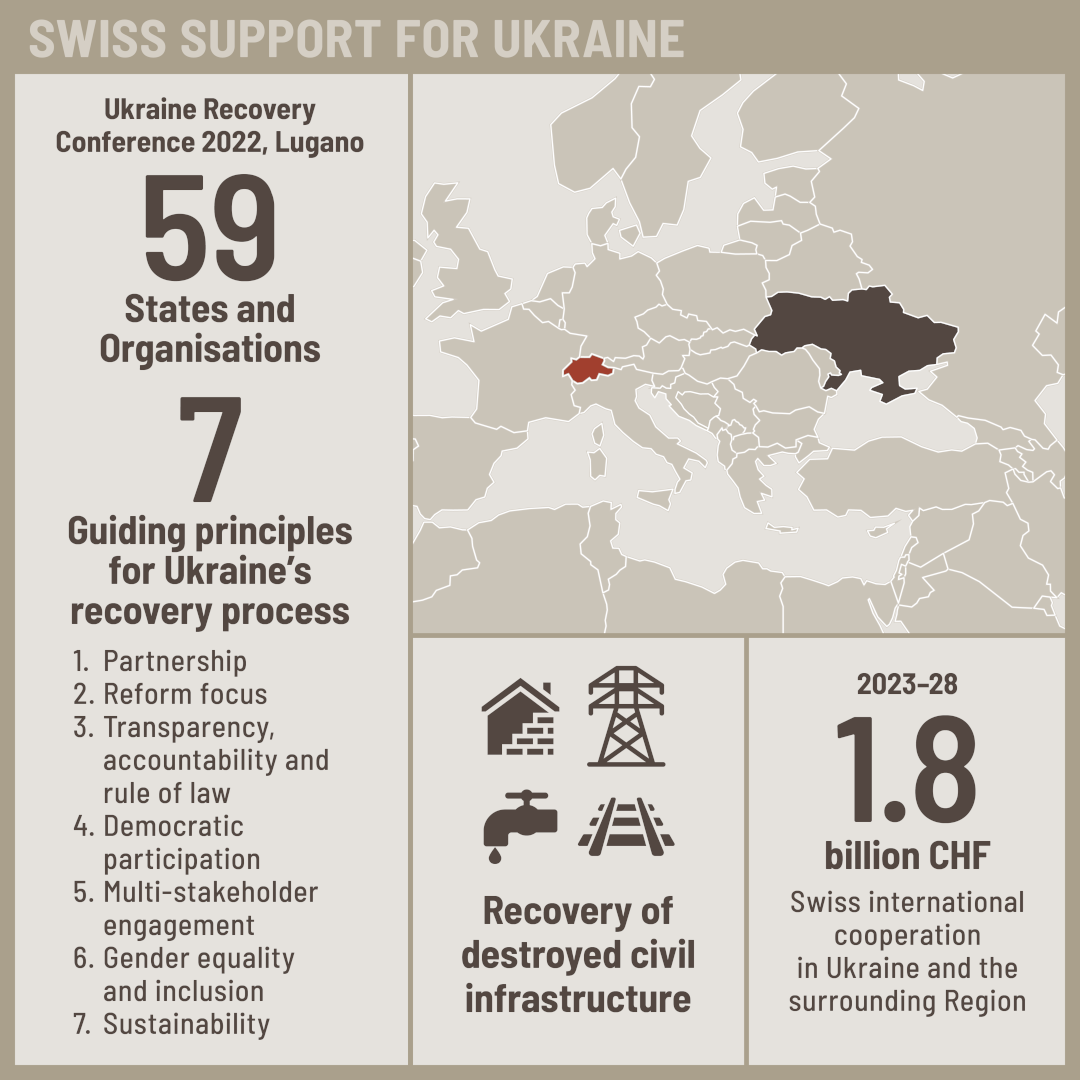 Swiss President Reasserts Support For Ukraine
May 02, 2025
Swiss President Reasserts Support For Ukraine
May 02, 2025
