Chief Election Commissioner Confident In Robust Poll Data System
Table of Contents
The Architecture of the Robust Poll Data System
The success of any election hinges on efficient data management. This robust poll data system is designed with real-time data processing and security at its core. Its architecture incorporates several key features designed to ensure accuracy and prevent manipulation:
-
Real-time Data Updates from Polling Stations: Data from polling stations is transmitted securely and processed in real-time, providing near-instantaneous updates on voter turnout and vote counts. This minimizes delays and allows for swift identification and resolution of any discrepancies.
-
Secure Data Transmission Protocols: The system utilizes advanced encryption methods, such as AES-256 encryption, to protect data during transmission. This prevents unauthorized access and ensures the confidentiality of sensitive election information.
-
Redundant Systems to Prevent Data Loss: Multiple backup systems and geographically distributed servers are in place to safeguard against data loss due to technical failures or natural disasters. This redundancy ensures the continuous operation of the system, even under challenging circumstances.
-
Robust Data Validation and Verification Processes: Rigorous data validation checks are implemented at each stage of the process, ensuring data accuracy and consistency. This includes cross-checking data from multiple sources and employing sophisticated algorithms to detect and flag any inconsistencies.
-
Integration with Voter Databases for Accuracy: The system seamlessly integrates with comprehensive voter databases, allowing for efficient verification of voter eligibility and prevention of duplicate voting. This integration ensures the accuracy and integrity of the election results.
Security Measures Implemented to Protect Election Data
The security of election data is paramount. This system employs multiple layers of protection to mitigate risks and prevent data breaches or manipulation:
-
Multi-layered Security Protocols: A multi-layered security approach incorporates firewalls, intrusion detection systems, and other security technologies to create a robust defense against cyberattacks.
-
Strict Access Control Measures: Access to the system is strictly limited to authorized personnel only, using strong authentication mechanisms such as multi-factor authentication. This minimizes the risk of unauthorized access and data tampering.
-
Regular Security Audits and Penetration Testing: The system undergoes regular security audits and penetration testing by independent cybersecurity experts to identify and address potential vulnerabilities. This proactive approach ensures the ongoing security and resilience of the system.
-
Incident Response Plan in Case of a Security Breach: A comprehensive incident response plan is in place to handle any potential security breaches. This plan outlines procedures for containing the breach, investigating its cause, and restoring system integrity.
-
Data Encryption at Rest and in Transit: Data encryption is employed both while data is stored (at rest) and during transmission (in transit), protecting it from unauthorized access even if intercepted.
Addressing Concerns Regarding Data Integrity and Transparency
Maintaining data integrity and transparency is crucial to building public trust. The system addresses potential concerns through several key mechanisms:
-
Public Access to Aggregated Data: Aggregated data, while protecting individual voter privacy, is made available to the public, ensuring transparency in the election process.
-
Clear and Detailed Audit Trails: Detailed audit trails of all data modifications are maintained, providing a complete record of all actions taken on the system. This allows for scrutiny and accountability.
-
Independent Audits of the System: Independent audits of the system are conducted regularly to verify the accuracy, security, and integrity of the poll data system.
-
Mechanisms for Addressing Discrepancies and Resolving Disputes: Clearly defined procedures are in place to handle discrepancies and resolve disputes that may arise during the election process.
The Chief Election Commissioner's Statement and Rationale
The Chief Election Commissioner stated, “[Insert direct quote from the Chief Election Commissioner expressing confidence in the system].” This confidence stems from the robust architecture and comprehensive security measures implemented within the poll data system. The real-time data updates, secure transmission protocols, and rigorous data validation processes contribute significantly to the accuracy and reliability of the election results. This, in turn, strengthens voter confidence and reinforces public trust in the integrity of the election process.
Conclusion
The robust poll data system, with its advanced architecture, multi-layered security, and commitment to transparency, plays a critical role in ensuring fair and transparent elections. The Chief Election Commissioner's confidence in this system reflects its proven capabilities and the dedication to maintaining the highest standards of election integrity. This system, by bolstering election data security and transparency, directly contributes to a more trustworthy and democratic electoral process. Learn more about the robust poll data system and its role in ensuring fair elections by visiting [link to relevant website].

Featured Posts
-
 India Reasserts Justice Demand Following Rubios De Escalation Appeal
May 02, 2025
India Reasserts Justice Demand Following Rubios De Escalation Appeal
May 02, 2025 -
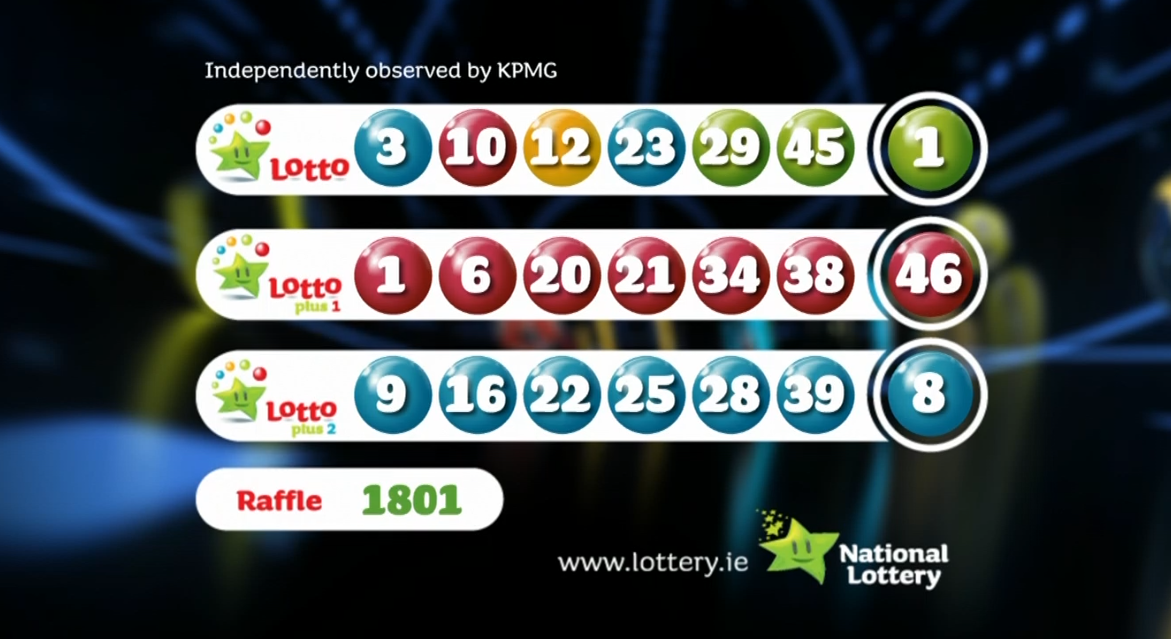 Winning Numbers Lotto Lotto Plus 1 And Lotto Plus 2 Draws
May 02, 2025
Winning Numbers Lotto Lotto Plus 1 And Lotto Plus 2 Draws
May 02, 2025 -
 Six Nations Irelands Next Opponent France Issues A Warning
May 02, 2025
Six Nations Irelands Next Opponent France Issues A Warning
May 02, 2025 -
 Christina Aguileras Dramatic Change A Look At Her Evolving Image
May 02, 2025
Christina Aguileras Dramatic Change A Look At Her Evolving Image
May 02, 2025 -
 Dash Rendar Action Figure Hasbros Star Wars Shadow Of The Empire Release
May 02, 2025
Dash Rendar Action Figure Hasbros Star Wars Shadow Of The Empire Release
May 02, 2025
