Block Mirror: Bypassing Censorship And Accessing Blocked Content

Table of Contents
How Block Mirrors Work: Understanding the Technology
The Mechanics of Mirroring
Block mirrors function by creating identical copies of websites on different servers, located in regions where the original content isn't blocked. This mirroring process ensures that even if access to the original site is restricted, the mirrored version remains available. Proxies and VPNs often play a crucial role. A proxy server acts as an intermediary, masking your IP address and routing your request through a different server, ultimately accessing the block mirror. VPNs provide an even higher level of security by encrypting your internet traffic, further protecting your anonymity and privacy while circumventing censorship. While the technical details involve DNS manipulation (redirecting domain name requests) and HTTP requests (the language your browser uses to communicate with websites), understanding these specifics isn't necessary for effective use.
- Replication of website data: The entire website, or key sections, are copied to a different server.
- Proxy server redirection: Your request is routed through a proxy server to mask your location.
- DNS resolution changes: The DNS server you use might be configured to point to the mirror server.
- Encrypted connections: Using HTTPS on the mirror site and a VPN encrypts communication.
Types of Block Mirrors
There are various types of block mirrors, each with its advantages and disadvantages:
- Static Mirrors: These are simple copies of a website at a specific point in time. They are easy to set up but don't update automatically, meaning they may become outdated quickly.
- Dynamic Mirrors: These mirrors automatically update to reflect changes on the original website, ensuring users always access the latest content. However, they require more complex technology to maintain.
- Distributed Mirrors: These distribute website copies across multiple servers in different geographic locations. This increases reliability and resilience, making it harder for censorship efforts to completely shut down access. If one mirror goes down, others remain accessible.
Accessing Blocked Content Using Block Mirrors: A Practical Guide
Choosing a Reliable Block Mirror
Security and privacy are paramount when selecting a block mirror. Never use a mirror that doesn't use HTTPS, as this makes your connection vulnerable. Always check user reviews and testimonials to gauge the reliability and trustworthiness of the service. Consider the server location; a mirror closer to your geographical location will usually offer faster speeds and lower latency.
- Check for HTTPS: Ensure the website uses secure HTTPS protocol.
- Read reviews and testimonials: Look for feedback from other users.
- Verify server location: A geographically closer server is preferable for speed and performance.
- Avoid suspicious sites: Beware of sites with poor design, excessive ads, or suspicious activities.
Safety Precautions When Using Block Mirrors
Accessing blocked content carries risks. Always take necessary precautions:
- Malware Risks: Insecure block mirrors can host malware. Use reputable antivirus software.
- Privacy Concerns: Using a VPN alongside a block mirror significantly enhances your anonymity and protects your privacy. Your real IP address remains hidden.
- Legal Considerations: Accessing blocked content may have legal implications in your region. Be aware of your local laws and regulations.
Always use reputable antivirus software and be cautious of suspicious links or downloads.
Alternatives to Block Mirrors for Accessing Blocked Content
While block mirrors are effective, other methods exist to circumvent censorship, each with its strengths and weaknesses:
- VPNs (Virtual Private Networks): Encrypt your internet traffic and mask your IP address, providing strong privacy and security. They are widely available but can be slower than direct connections.
- Tor: A more anonymous but slower method that routes your traffic through multiple servers, making it difficult to trace your online activity. Best for accessing highly sensitive content.
- Proxy Servers: Similar to VPNs but generally offer less security and privacy.
Conclusion: Choosing the Right Approach for Unblocking Content
Block mirrors provide a valuable tool for accessing information restricted by censorship. However, it’s crucial to prioritize online safety and privacy. Using a VPN in conjunction with a block mirror is a strong recommendation. Consider the risks involved and choose the method that best balances your need for access with your security concerns. Explore the power of block mirrors to access information freely, but always prioritize your online safety and privacy. Learn more about secure methods for accessing blocked content today!

Featured Posts
-
 Lafc Vs San Jose A Pivotal Mls Game
May 16, 2025
Lafc Vs San Jose A Pivotal Mls Game
May 16, 2025 -
 Political Fallout Warrens Handling Of Questions Regarding Bidens Health
May 16, 2025
Political Fallout Warrens Handling Of Questions Regarding Bidens Health
May 16, 2025 -
 Vont Weekend At 104 5 The Cat A Photo Journal April 4 6 2025
May 16, 2025
Vont Weekend At 104 5 The Cat A Photo Journal April 4 6 2025
May 16, 2025 -
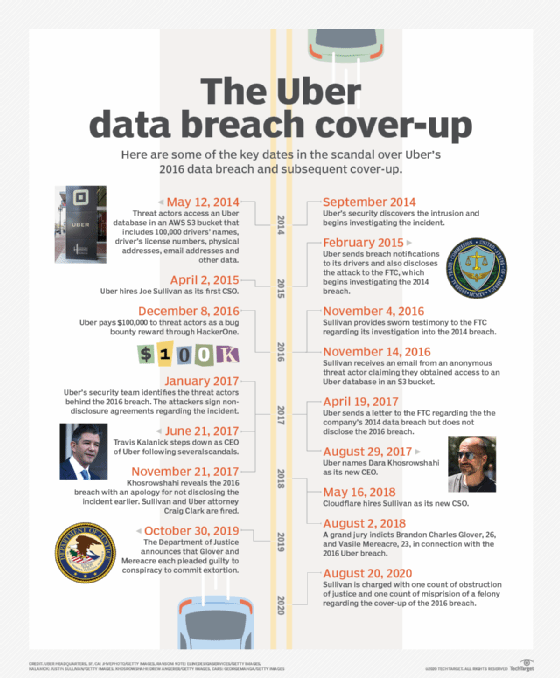 16 Million Penalty For T Mobile A Three Year Data Breach Timeline
May 16, 2025
16 Million Penalty For T Mobile A Three Year Data Breach Timeline
May 16, 2025 -
 Thoi Gian Xong Hoi Phu Hop Loi Ich Va Nhung Luu Y Quan Trong
May 16, 2025
Thoi Gian Xong Hoi Phu Hop Loi Ich Va Nhung Luu Y Quan Trong
May 16, 2025
Latest Posts
-
 Data Breach Costs T Mobile 16 Million Three Year Security Lapse Results In Fine
May 17, 2025
Data Breach Costs T Mobile 16 Million Three Year Security Lapse Results In Fine
May 17, 2025 -
 Creatine Benefits Side Effects And How To Use It
May 17, 2025
Creatine Benefits Side Effects And How To Use It
May 17, 2025 -
 Geopolitical Tensions Rise The Rare Earth Minerals Factor
May 17, 2025
Geopolitical Tensions Rise The Rare Earth Minerals Factor
May 17, 2025 -
 Rare Earth Minerals And The Emerging Cold War
May 17, 2025
Rare Earth Minerals And The Emerging Cold War
May 17, 2025 -
 From Scatological Documents To Podcast Gold An Ai Driven Approach
May 17, 2025
From Scatological Documents To Podcast Gold An Ai Driven Approach
May 17, 2025
